#FactCheck: AI Generated audio of CDS admitting that Pakistan Army is superior than Indian Army.
Executive Summary:
A viral social media claim alleges that India’s Chief of Defence Staff (CDS), General Anil Chauhan, praised Pakistan’s Army as superior during “Operation Sindoor.” Fact-checking confirms the claim is false. The original video, available on The Hindu’s official channel, shows General Chauhan inaugurating Ran-Samwad 2025 in Mhow, Madhya Pradesh. At the 1:22:12 mark, the genuine segment appears, proving the viral clip was altered. Additionally, analysis using Hiya AI Audio identified voice manipulation, flagging the segment as a deepfake with an authenticity score of 1/100. The fabricated statement was: “never mess with Pakistan because their army appears to be far more superior.” Thus, the viral video is doctored and misleading.
Claim:
A viral claim is being shared on social media (archived link) falsely claiming that India’s Chief of Defence Staff (CDS), General Anil Chauhan described Pakistan’s Army as superior and more advanced during Operation Sindoor.

Fact Check:
After performing a reverse image search we found a full clip on the official channel of The Hindu in which Chief of Defence Staff Anil Chauhan inaugurated ‘Ran-Samwad’ 2025 in Mhow, Madhya Pradesh.

In the clip on the time stamp of 1:22:12 we can see the actual part of the video segment which was manipulated in the viral video.
Also, by using Hiya AI Audio tool we got to know that the voice was manipulated in the specific segment of the video. The result shows Deepfake with an authenticity score 1/100, the result also shows the statement which is deepfake which was “ was to never mess with Pakistan because their army appears to be far more superior”.
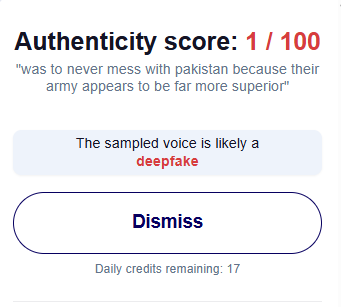
Conclusion:
The viral video attributing remarks to CDS General Anil Chauhan about Pakistan’s Army being “superior” is fabricated. The original footage from The Hindu confirms no such statement was made, while forensic analysis using Hiya AI Audio detected clear voice manipulation, identifying the clip as a deepfake with minimal authenticity. Hence, the claim is baseless, misleading, and an attempt to spread disinformation.
- Claim: AI Generated audio of CDS admitting that the Pakistan Army is superior to the Indian Army.
- Claimed On: Social Media
- Fact Check: False and Misleading
Related Blogs

Introduction
With the increasing frequency and severity of cyber-attacks on critical sectors, the government of India has formulated the National Cyber Security Reference Framework (NCRF) 2023, aimed to address cybersecurity concerns in India. In today’s digital age, the security of critical sectors is paramount due to the ever-evolving landscape of cyber threats. Cybersecurity measures are crucial for protecting essential sectors such as banking, energy, healthcare, telecommunications, transportation, strategic enterprises, and government enterprises. This is an essential step towards safeguarding these critical sectors and preparing for the challenges they face in the face of cyber threats. Protecting critical sectors from cyber threats is an urgent priority that requires the development of robust cybersecurity practices and the implementation of effective measures to mitigate risks.
Overview of the National Cyber Security Policy 2013
The National Cyber Security Policy of 2013 was the first attempt to address cybersecurity concerns in India. However, it had several drawbacks that limited its effectiveness in mitigating cyber risks in the contemporary digital age. The policy’s outdated guidelines, insufficient prevention and response measures, and lack of legal implications hindered its ability to protect critical sectors adequately. Moreover, the policy should have kept up with the rapidly evolving cyber threat landscape and emerging technologies, leaving organisations vulnerable to new cyber-attacks. The 2013 policy failed to address the evolving nature of cyber threats, leaving organisations needing updated guidelines to combat new and sophisticated attacks.
As a result, an updated and more comprehensive policy, the National Cyber Security Reference Framework 2023, was necessary to address emerging challenges and provide strategic guidance for protecting critical sectors against cyber threats.

Highlights of NCRF 2023
Strategic Guidance: NCRF 2023 has been developed to provide organisations with strategic guidance to address their cybersecurity concerns in a structured manner.
Common but Differentiated Responsibility (CBDR): The policy is based on a CBDR approach, recognising that different organisations have varying levels of cybersecurity needs and responsibilities.
Update of National Cyber Security Policy 2013: NCRF supersedes the National Cyber Security Policy 2013, which was due for an update to align with the evolving cyber threat landscape and emerging challenges.
Different from CERT-In Directives: NCRF is distinct from the directives issued by the Indian Computer Emergency Response Team (CERT-In) published in April 2023. It provides a comprehensive framework rather than specific directives for reporting cyber incidents.
Combination of robust strategies: National Cyber Security Reference Framework 2023 will provide strategic guidance, a revised structure, and a proactive approach to cybersecurity, enabling organisations to tackle the growing cyberattacks in India better and safeguard critical sectors. Rising incidents of malware attacks on critical sectors
In recent years, there has been a significant increase in malware attacks targeting critical sectors. These sectors, including banking, energy, healthcare, telecommunications, transportation, strategic enterprises, and government enterprises, play a crucial role in the functioning of economies and the well-being of societies. The escalating incidents of malware attacks on these sectors have raised concerns about the security and resilience of critical infrastructure.
Banking: The banking sector handles sensitive financial data and is a prime target for cybercriminals due to the potential for financial fraud and theft.
Energy: The energy sector, including power grids and oil companies, is critical for the functioning of economies, and disruptions can have severe consequences for national security and public safety.
Healthcare: The healthcare sector holds valuable patient data, and cyber-attacks can compromise patient privacy and disrupt healthcare services. Malware attacks on healthcare organisations can result in the theft of patient records, ransomware incidents that cripple healthcare operations, and compromise medical devices.
Telecommunications: Telecommunications infrastructure is vital for reliable communication, and attacks targeting this sector can lead to communication disruptions and compromise the privacy of transmitted data. The interconnectedness of telecommunications networks globally presents opportunities for cybercriminals to launch large-scale attacks, such as Distributed Denial-of-Service (DDoS) attacks.
Transportation: Malware attacks on transportation systems can lead to service disruptions, compromise control systems, and pose safety risks.
Strategic Enterprises: Strategic enterprises, including defence, aerospace, intelligence agencies, and other sectors vital to national security, face sophisticated malware attacks with potentially severe consequences. Cyber adversaries target these enterprises to gain unauthorised access to classified information, compromise critical infrastructure, or sabotage national security operations.
Government Enterprises: Government organisations hold a vast amount of sensitive data and provide essential services to citizens, making them targets for data breaches and attacks that can disrupt critical services.

Conclusion
The sectors of banking, energy, healthcare, telecommunications, transportation, strategic enterprises, and government enterprises face unique vulnerabilities and challenges in the face of cyber-attacks. By recognising the significance of safeguarding these sectors, we can emphasise the need for proactive cybersecurity measures and collaborative efforts between public and private entities. Strengthening regulatory frameworks, sharing threat intelligence, and adopting best practices are essential to ensure our critical infrastructure’s resilience and security. Through these concerted efforts, we can create a safer digital environment for these sectors, protecting vital services and preserving the integrity of our economy and society. The rising incidents of malware attacks on critical sectors emphasise the urgent need for updated cybersecurity policy, enhanced cybersecurity measures, a collaboration between public and private entities, and the development of proactive defence strategies. National Cyber Security Reference Framework 2023 will help in addressing the evolving cyber threat landscape, protect critical sectors, fill the gaps in sector-specific best practices, promote collaboration, establish a regulatory framework, and address the challenges posed by emerging technologies. By providing strategic guidance, this framework will enhance organisations’ cybersecurity posture and ensure the protection of critical infrastructure in an increasingly digitised world.
.webp)
What is Deepfake
Deepfakes have been, a fascinating but unsettling phenomenon that is now prominent in this digital age. These incredibly convincing films have drawn attention and blended in well with our high-tech surroundings. The lifelike but completely manufactured quality of deepfake videos has become an essential component of our digital environment as we traverse the broad reaches of our digital society. While these works have an undoubtedly captivating charm, they have important ramifications. Come along as we examine the deep effects that misuse of deepfakes can have on our globalized digital culture. After many actors now business tycoon Ratan Tata has become the latest victim of deepfake. Tata called out a post from a user that used a fake interview of him in a video recommending Investments.
Case Study
The nuisance of deep fake is sparing none from actors politicians to entrepreneurs everyone is getting caught in the Trap. Soon after the actresses Rashmika Mandana, Katrina Kaif, Kajol and other actresses fell prey to the rising scenario of deepfake, a new case from the industry emerged, which took Mr. Ratan Tata on storm. Business tycoon Ratan Tata has become the latest victim of deepfake. He took to his social media sharing an image of the interview that asked people to invest money in a project in a post on Instagram. Ratan Tata called out a post from a user that used a fake interview of him in a video recommending these Investments.
This nuisance that has been created because of the deepfake is sparing nobody from actors to politicians to entrepreneurs now everyone is getting caught in the trap the latest victim being Ratan Tata. Tech magnate Ratan Tata is the most recent victim of this deepfake phenomenon. The millionaire was seen in the video, which was posted by the Instagram user, giving his followers a once-in-a-million opportunity to "exaggerate investments risk-free."
In the stated video, Ratan Tata was seen giving everyone in India advice mentioning to the public regarding the opportunity to increase their money with no risk and a 100% guarantee. The caption of the video clip stated, "Go to the channel right now."
Tata annotated both the video and the screenshot of the caption with the word "FAKE."
Ongoing Deepfake Assaults in India
Deepfake videos continue to target celebrities, and Priyanka Chopra is also a recent victim of this unsettling trend. Priyanka's deepfake adopts a different strategy than other examples, including actresses like Rashmika Mandanna, Katrina Kaif, Kajol, and Alia Bhatt. Rather than editing her face in contentious situations, the misleading film keeps her looking the same but modifies her voice and replaces real interview quotes with made-up commercial phrases. The deceptive video shows Priyanka promoting a product and talking about her yearly salary, highlighting the worrying development of deepfake technology and its possible effects on prominent personalities.
Prevention and Detection
In order to effectively combat the growing threat posed by deepfake technology, people and institutions should place a high priority on developing critical thinking abilities, carefully examining visual and auditory cues for discrepancies, making use of tools like reverse image searches, keeping up with the latest developments in deepfake trends, and rigorously fact-check reputable media sources. Important actions to improve resistance against deepfake threats include putting in place strong security policies, integrating cutting-edge deepfake detection technologies, supporting the development of ethical AI, and encouraging candid communication and cooperation. We can all work together to effectively and mindfully manage the problems presented by deepfake technology by combining these tactics and making adjustments to the constantly changing terrain.
Conclusion
The current instance involving Ratan Tata serves as an example of how the emergence of counterfeit technology poses an imminent danger to our digital civilization. The fake video, which was posted to Instagram, showed the business tycoon giving financial advice and luring followers with low-risk investment options. Tata quickly called out the footage as "FAKE," highlighting the need for careful media consumption. The Tata incident serves as a reminder of the possible damage deepfakes can do to prominent people's reputations. The issue, in Ratan Tata's instance specifically, demands that public personalities be more mindful of the possible misuse of their virtual identities. We can all work together to strengthen our defenses against this sneaky phenomenon and maintain the trustworthiness of our internet-based culture in the face of ever-changing technological challenges by emphasizing preventive measures like strict safety regulations and the implementation of state-of-the-art deepfake detection technologies.
References
- https://economictimes.indiatimes.com/magazines/panache/ratan-tata-slams-deepfake-video-that-features-him-giving-risk-free-investment-advice/articleshow/105805223.cms
- https://www.ndtv.com/india-news/ratan-tata-flags-deepfake-video-of-his-interview-recommending-investments-4640515
- https://www.businesstoday.in/bt-tv/short-video/viralvideo-business-tycoon-ratan-tata-falls-victim-to-deepfake-408557-2023-12-07
- https://www.livemint.com/news/india/false-ratan-tata-calls-out-a-deepfake-video-of-him-giving-investment-advice-11701926766285.html
%203rd%20Sep%2C%202025.webp)
In the past decade, India’s gaming sector has seen a surprising but swift advancement, which brought along millions of players and over billions in investments and has even been estimated to be at $23 billion. Whether it's fantasy cricket and Ludo apps, high-stakes poker, or rummy platforms, investing real money in online gaming and gambling has become a beloved hobby for many. Moreover, it not only gave a boost to the economy but also contributed to creative innovation and the generation of employment.
The real concern lies behind the glossy numbers, tales of addiction, financial detriment, and the never-ending game of cat and mouse with legal loopholes. The sector’s meteoric rise has raised various concerns relating to national financial integrity, regulatory clarity and consumer safety.
In light of this, the Promotion and Regulation of Online Gaming Act, 2025, which was passed by Parliament and signed into law on August 22, stands out as a significant development. The Act, which is positioned as a consumer protection and sector-defining law, aims to distinguish between innovation and exploitation by acknowledging e-sport as a legitimate activity and establishing unambiguous boundaries around the larger gaming industry.
Key Highlights of the Act
- Complete Ban on all games involving Real-Money: All e-games, whether based on skill or luck, that involve monetary stakes have been banned.
- Prohibition of Ads: Promotion of such e-games has also been disallowed across all platforms.
- Legal Ramifications: Operation of such games may lead to up to 3 years in prison with a 1 cr fine; Advertisement for the same may lead to up to 2 years in prison with a 50 lakh fine. However, in case of repeat offences, this may go up to 3-5 years in prison and 2 cr in fines.
- Creation of Online Gaming Authority: The creation of a national-level regulatory body to classify and monitor games, register platforms and enforce the dedicated rules.
- Support for eSports and Social & Educational games: All kinds of games that are non-monetary, promote social and educational growth, will not only be recognised but encouraged. Meanwhile, eSports will also gain official recognition under the Ministry of Sports.
Positive Impacts
- Addressal & Tackling of Addiction and Financial Ruin: The major reason behind the ban is to reduce the cases of players, mainly youth, getting into gambling and losing huge amounts of money to betting apps and games, and to protect vulnerable users
- Boost to eSports & Regulatory Clarity: The law not only legitimises the eSport sector but also provides opportunities for scholarship and other financial benefits, along with windows for professional tournaments and platforms on global stages. Along with this aims to bring about an order around e-games of skill versus luck.
- Fraud Monitoring & Control: The law makes sure to block off avenues for money laundering, gambling and illegal betting networks.
- Promotion of Safe Digital Ecosystem: Encouraging social, developmental and educational games to focus on skill, learning and fun.
Challenges
The fact that the Promotion and Regulation of Online Gaming Act, 2025 is still in its early stages, which must be recognised. In the end, its effectiveness will rely not only on the letter of the law but on the strength of its enforcement and the wisdom of its application. The Act has the potential to safeguard the interests of at-risk youth from the dangers of gambling and its addiction, if it is applied carefully and clearly, all the while maintaining the digital ecosystem as a place of innovation, equity, and trust.
- Blanket Ban: By imposing a blanket ban on games that have long been justified as skill-based like rummy or fantasy cricket, the Act runs the risk of suppressing respectable enterprises and centres of innovation. Many startups that were once hailed for being at the forefront of India’s digital innovation may now find it difficult to thrive in an unpredictable regulatory environment.
- Rise of Illegal Platforms: History offers a sobering lesson, prohibition does not eliminate demand, it simply drives it underground. The prohibition of money games may encourage the growth of unregulated, offshore sites, where players are more vulnerable to fraud, data theft, and abuse and have no way to seek consumer protection.
Conclusion
The Act is definitely a tough and bold stand to check and regulate India’s digital gaming industry, but it is also a double-edged sword. It brings in much-needed consumer protection regulations in place and legitimises e-Sports. However, it also casts a long shadow over a successful economy and runs the risk of fostering a black market that is more harmful than the issue it was intended to address.
Therefore, striking a balance between innovation and protection, between law and liberty, will be considered more important in the coming years than the success of regulations alone. India’s legitimacy as a digital economy ready for global leadership, as well as the future of its gaming industry, will depend on how it handles this delicate balance.
References:
- https://economictimes.indiatimes.com/tech/technology/gaming-bodies-write-to-amit-shah-urge-to-block-blanket-ban-warn-of-rs-20000-crore-tax-loss/articleshow/123392342.cms
- https://m.economictimes.com/news/india/govt-estimates-45-cr-people-lose-about-rs-20000-cr-annually-from-real-money-gaming/articleshow/123408237.cms
- https://www.cyberpeace.org/resources/blogs/promotion-and-regulation-of-online-gaming-bill-2025-gets-green-flag-from-both-houses-of-parliament
- https://www.thehindu.com/business/Industry/real-money-gaming-firms-wind-down-operations/article69965196.ece


