#FactCheck – Elephant Falls From Truck? No, This Elephant Fall Video Is AI-Manipulated
Executive Summary:
A video circulating on social media claims to show a live elephant falling from a moving truck due to improper transportation, followed by the animal quickly standing up and reacting on a public road. The content may raise concerns related to animal cruelty, public safety, and improper transport practices. A detailed examination using AI content detection tools, visual anomaly analysis indicates that the video is not authentic and is likely AI generated or digitally manipulated.
Claim:
The viral video (archive link) shows a disturbing scene where a large elephant is allegedly being transported in an open blue truck with barriers for support. As the truck moves along the road, the elephant shifts its weight and the weak side barrier breaks. This causes the elephant to fall onto the road, where it lands heavily on its side. Shortly after, the animal is seen getting back on its feet and reacting in distress, facing the vehicle that is recording the incident. The footage may raise serious concerns about safety, as elephants are normally transported in reinforced containers, and such an incident on a public road could endanger both the animal and people nearby.
Fact Check:
After receiving the video, we closely examined the visuals and noticed some inconsistencies that raised doubts about its authenticity. In particular, the elephant is seen recovering and standing up unnaturally quickly after a severe fall, which does not align with realistic animal behavior or physical response to such impact.
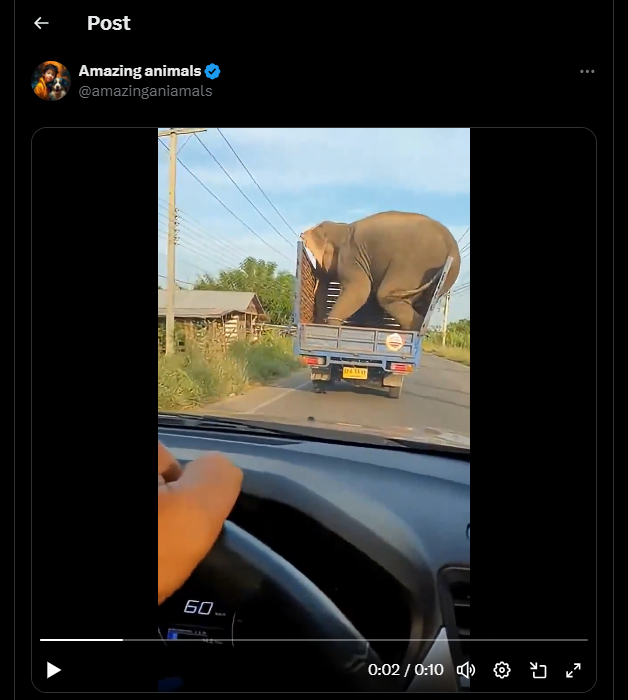
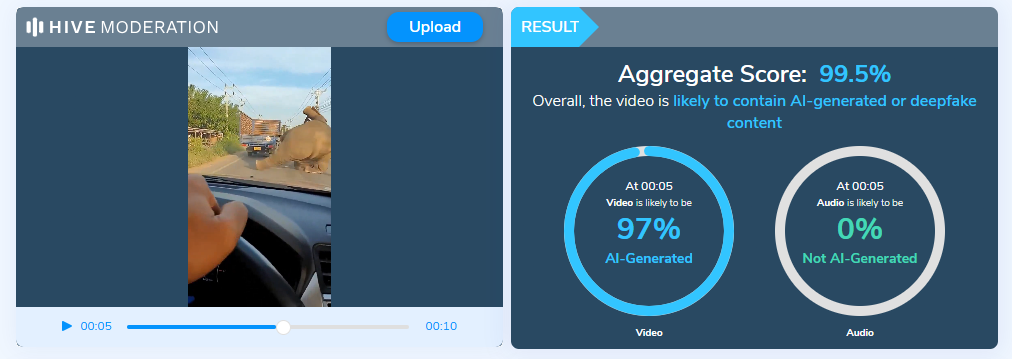
To further verify our observations, the video was analyzed using the Hive Moderation AI Detection tool, which indicated that the content is likely AI generated or digitally manipulated.
Additionally, no credible news reports or official sources were found to corroborate the incident, reinforcing the conclusion that the video is misleading.
Conclusion:
The claim that the video shows a real elephant transport accident is false and misleading. Based on AI detection results, observable visual anomalies, and the absence of credible reporting, the video is highly likely to be AI generated or digitally manipulated. Viewers are advised to exercise caution and verify such sensational content through trusted and authoritative sources before sharing.
- Claim: The viral video shows an elephant allegedly being transported, where a barrier breaks as it moves, causing the animal to fall onto the road before quickly getting back on its feet.
- Claimed On: X (Formally Twitter)
- Fact Check: False and Misleading
Related Blogs

Introduction
Social media has become integral to our lives and livelihood in today’s digital world. Influencers are now strong people who shape trends, views, and consumer behaviour. Influencers have become targets for bad actors aiming to abuse their fame due to their significant internet presence. Unfortunately, account hacking has grown frequently, with significant ramifications for influencers and their followers. Furthermore, the emergence of social media platforms in recent years has opened the way for influencer culture. Influencers exert power over their followers’ ideas, lifestyle choices, and purchase decisions. Influencers and brands frequently collaborate to exploit their reach, resulting in a mutually beneficial environment. As a result, the value of influencer accounts has risen dramatically, attracting the attention of hackers trying to abuse their potential for financial gain or personal advantage.
Instances of recent attacks
Places of worship
The hackers have targeted renowned temples for fulfilling their malicious activities the recent attack happened on The Khautji Shyam Temple, a famous religious institution with enormous cultural and spiritual value for its adherents. It serves as a place of worship, community events, and numerous religious activities. However, since technology has invaded all sectors of life, the temple’s online presence has developed, giving worshippers access to information, virtual darshans (holy viewings), and interactive forums. Unfortunately, this digital growth has also rendered the shrine vulnerable to cyber threats. The hackers hacked the Facebook page twice in the month, demanded donations and hacked the cheques the devotes gave to the trust. The second event happened by posting objectional images on the page and hurting the sentiments of the devotees. The Committee of the temple has filed an FIR under various charges and is also seeking help from the cyber cell.
Social media Influencers
Influencers enjoy a vast online following worldwide, but their presence is limited to the digital space. Hence every video, photo is of importance to them. An incident took place with leading news anchor and reporter Barkha Dutt, where in her youtube channel was hacked into, and all the posts made from the channel were deleted. The hackers also replaced the channel’s logo with Tesla and were streaming a live video on the channel featuring Elon Musk. A similar incident was reported by influencer Tanmay Bhatt, who also lost all the content e had posted on his channel. The hackers use the following methods to con social media influencers:
- Social engineering
- Phishing
- Brute Force Attacks
Such attacks on influencers can cause harm to their reputation, can also cause financial loss, and even lose the trust of the viewers or the followers who follow them, thus further impacting the collaborations.

Safeguards
Social media influencers need to be very careful about their cyber security as their prominent presence is in the online world. The influencers from different platforms should practice the following safeguards to protect themselves and their content better online
Secure your accounts
Protecting your accounts with passphrases or strong passwords is the first step. The best strategy for doing this is to create a passphrase, a phrase only you know. We advise choosing a passphrase with at least four words and 15 characters.
To further secure your accounts, you must enable multi-factor authentication in the second step.
To access your account, a hacker must guess your password and provide a second authentication factor (such as a face scan or fingerprint) that matches yours.
Be careful about who has access
Many social media influencers collaborate with a team to help generate and post content while building their personal brands.
This entails using team members who can write and produce material that influencers can share themselves, according to some of them. In these situations, the influencer is the only person who still has access to the account.
There are more potential weak spots when more people have access. Additionally, it increases the number of ways a password or account access could fall into the hands of a cybercriminal. Only some staff members will be as cautious about password security as you may be.
Stay up-to-date on the threats
What’s the most significant way to combat threats to computer security? Information.
Cybercriminals constantly adapt their methods. It’s crucial to stay informed about these threats and how they can be utilised against you.
But it’s not just threats. Social media platforms and other service providers are likewise changing their offerings to avoid these challenges.
Educate yourself to protect yourself. You can keep one step ahead of the hazards that cybercriminals offer by continuously educating yourself.
Preach cybersecurity
As influencers, cyber security should be preached, no matter your agenda.
This will also enable users to inculcate best practices for digital hygiene.
This will also boost the reporting numbers and increase population awareness, thus eradicating such bad actors from our cyberspace.
Acknowledge the risks
Keeping a blind eye will always hurt the safety aspects, as ignorance always causes issues.
Risks should be kept in mind while creating the digital routine and netiquette
Always inform your users of risk existing and potential risks
Monitor threats
After the acknowledgement, it is essential to monitor threats.
Active lookout for threats will allow you to understand the modus Operandi and the vulnerabilities to avoid criminals
Threats monitoring is also a basic netizens’ responsibility to ensure that the threats are reported as they emerge.
Interpret the data
All cyber nodal agencies release data and trends of cybercrimes, understand the trends and protect your vulnerabilities.
Data interpretation can lead to an early flagging of threats and issues, thus protecting the cyber ecosystem by and large.
Create risk profiles
All influencers should create risk profiles and backup profiles.
This will also help protect one’s data as it can be stored on different profiles.
Risk profiles and having a private profile are essential to safeguard the basic cyber interests of an influencer.

Conclusion
As we go deeper into the digital age, we see more technologies emerging, but along with them, we see a new generation of cyber threats and challenges. The physical, as well as the cyberspace, is now inter twinned and interdependent. Practising basic cyber security practices, hygiene, netiquette, and monitoring best practices will go a long way in protecting the online interests of the Influencers and will impact their followers to engage in best practices thus safeguarding the cyber ecosystem at large.
.webp)
Introduction
In an era where digital connectivity drives employment, investment, and communication, the most potent weapon of cybercriminals is ‘gaining trust’ with their sophisticated tactics. Prayagraj has been a recent battleground in India's cybercrime landscape. Within a one-year crackdown, over 10,400 SIM cards, 612 mobile device IMEIs, and 59 bank accounts were blocked, exposing a sprawling international fraud network. These activities primarily targeted unsuspecting individuals through Telegram job postings, fake investment tips, and mobile app scams, highlighting the darker side of convenience in cyberspace. With India now experiencing a wave of scams enabled by technology, this crackdown establishes a precedent for concerted cyber policing and awareness among citizens.
Digital Deceit: How the Scams Operated
SIM cards that have been issued through fake or stolen identities are increasingly being used by cybercriminals in Prayagraj and elsewhere. These SIMs were the initial weapon in a highly organised fraud system, allowing criminals to conduct themselves anonymously while abusing messaging services like WhatsApp and Telegram. The gangs involved in these scams, some of which have been linked by reports to nations like Nepal, Pakistan, China, Dubai, and Myanmar, enticed their victims with rich-yielding stock market advice, remote employment offers, and weekend employment promises. After getting a target engaged, victims were slowly manipulated into sending money in the name of application fees, verification fees, or investment contributions.
API Abuse and OTP Interception
What's more alarming about these scams is their tech-savviness. From Prayagraj's cybercrime squad, several syndicates are reported to have employed API-based mobile applications to intercept OTPs (One-Time Passwords) sent to Indian numbers. Such apps, cleverly disguised as genuine services or work-from-home software, collected personal details like bank account credentials and payment card data, allowing wrongdoers to carry out unauthorised transactions in a matter of minutes. The pilfered funds were then quickly transferred through several mule accounts, rendering the money trail almost untraceable.
The Human Impact: How Citizens Were Trapped
Victims tended to come from job-hunting groups, students, or housewives seeking to earn additional income. Often, the scammers persuaded users to join Telegram channels providing free investment advice or job-referral-based schemes, creating an illusion of authenticity. Once on board, victims were sometimes even paid small commissions initially, creating a false sense of success. This tactic, known as “advance-fee confidence building,” made victims more likely to invest larger sums later, ultimately leading to complete financial loss.
Digital Arrest Threats and Bitcoin Ransom Scams
Aside from investment and job scam complaints, the cybercrime cell also saw several "digital arrest" scams, where victims were forced to send money under the threat of engaging in criminal activities. Bitcoin extortion schemes were also used in some cases, with perpetrators threatening exposure of victims' personal information or browsing history on the internet unless they were paid in cryptocurrency.
Law Enforcement’s Cyber Shield: Local Action, Global Impact
Identifying the extent of the threat, Prayagraj authorities implemented strategic measures to enable local policing. Cyber Units have been formed in each of the 43 police stations in the district, each made up of a sub-inspector, head constable, constable, lady constable, and computer operator. This decentralised model enables response in real-time, improved victim support, and quicker forensic analysis of hacked devices. The nodal officer for cyber operations said that this multi-level action is not punitive but preventive, meant to break syndicates before more harm is caused.
CyberPeace Recommendations: Prevention is Power
As cybercrime gets advanced, citizens will also have to keep pace with it. Prayagraj's experience highlights the importance of public awareness, digital literacy, and instant response processes. To assist in preventing people from falling victim to such scams, CyberPeace advises the following:
- Don't click on dubious APK links sent on WhatsApp or Telegram.
- Do not share OTPs or confidential details, even if the source appears to be familiar.
- Never download unfamiliar apps that demand access to SMS or financial information.
- Block your SIM card, payment cards, and bank accounts at once if your phone is stolen.
- Report all cyber frauds to cybercrime.gov.in or your local Cyber Cell.
- Never join investment or job groups on social sites without verification.
- Refuse video calls from unknown numbers; some scammers use this method of recording or blackmailing victims.
Conclusion
Prayagraj crackdown uncovers both the magnitude and versatility of cybercrime in the present. From trans-border cartels to Telegram job scams, the cyber front is as intricate as ever. But this incident also illustrates what can be achieved when technology, law enforcement, and public awareness come together. To stay safe from cyber threats, a cyber-conscious citizenry is as important as an effective cyber cell for India. At CyberPeace, we know that defending cyberspace begins with cyber resilience, and the story of Prayagraj should encourage communities everywhere to take active digital precautions.
References
- https://www.hindustantimes.com/cities/lucknow-news/over-10k-sims-blocked-as-job-investment-frauds-rise-in-prayagraj-101753715061234.html
- https://consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams
- https://faq.whatsapp.com/2286952358121083
- https://education.vikaspedia.in/viewcontent/education/digital-litercy/information-security/preventing-online-scams-cert-in-advisory?lgn=en
- https://cybercrime.gov.in/Accept.aspx
- https://www.linkedin.com/pulse/perils-advance-fee-fraud-protecting-yourself-from-scammers-sharma/

Today, let us talk about one of the key features of our digital lives – security. The safer their online habits are, the safer their data and devices will be. A branded security will make their devices and Internet connections secure, but their carelessness or ignorance can make them targets for cybercrimes. On the other hand, they can themselves unwittingly get involved in dubious activities online. With children being very smart about passwords and browsing history clearing, parents are often left in the dark about their digital lives.
Fret not, parental controls are there at your service. These are digital tools often included with your OS or security software package, which helps you to remotely monitor and control your child’s online activities.
Where Can I find them?
Many devices come with pre-installed PC tools that you have to set up and run. Go to Settings-> Parental controls or Screentime and proceed from there. As I mentioned, they are also offered as a part of your comprehensive security software package.
Why and How to Use Parental Controls
Parental controls help monitor and limit your children's smartphone usage, ensuring they access only age-appropriate content. If your child is a minor, use of this tool is recommended, with the full knowledge of your child/ren. Let them know that just as you supervise them in public places for their safety, and guide them on rights and wrongs, you will use the tool to monitor and mentor them online, for their safety. Emphasize that you love them and trust them but are concerned about the various dubious and fake characters online as well as unsafe websites and only intend to supervise them. As they grow older and display greater responsibility and maturity levels, you may slowly reduce the levels of monitoring. This will help build a relationship of mutual trust and respect.
Step 1: Enable Parental Controls
- iOS: If your child has an iPhone, to set up the controls, go to Settings, select Screen Time, then select Content & Privacy Restrictions.
- Android: If the child has an Android phone, you can use the Google Family Link to manage apps, set screen time limits, and track device usage.
- Third-party apps: Consider security tools like McAfee, Kaspersky, Bark, Qustodio, or Norton Family for advanced features.
Check out what some of the security software apps have on offer:





If you prefer Norton, here are the details:
McAfee Parental Controls suite offers the following features:

McAfee also outlines why Parental Controls matter:

Lastly, let us take a look at what Quick Heal has on offer:

STEP 2: Set up Admin Login
Needless to say, a parent should be the admin login, and it is a wise idea to set up a strong and unique password. You do not want your kids to outsmart you and change their accessibility settings, do you? Remember to create a password you will remember, for children are clever and will soon discover where you have jotted it down.
STEP 3: Create Individual accounts for all users of the device
Let us say two minor kids, a grandparent and you, will be using the device. You will have to create separate accounts for each user. You can allow the children to choose their own passwords, it will give them a sense of privacy. The children or you may (or may not) need to help any Seniors set up their accounts.
Done? Good. Now let us proceed to the next step.
STEP 4: Set up access permissions by age
Let us first get grandparents and other seniors out of the way by giving them full access. when you enter their ages; your device will identify them as adults and guide you accordingly.
Now for each child, follow the instructions to set up filters and blocks. This will again vary with age – more filters for the younger ones, while you can remove controls gradually as they grow older, and hence more mature and responsible. Set up screen Time (daily and weekends), game filtering and playtime, content filtering and blocking by words (e.g. block websites that contain violence/sex/abuse). Ask for activity reports on your device so that you can monitor them remotely This will help you to receive alerts if children connect with strangers or get involved in abusive actions.
Save the data and it has done! Simple, wasn’t it?
Additional Security
For further security, you may want to set up parental controls on the Home Wi-Fi Router, Gaming devices, and online streaming services you subscribe to.
Follow the same steps. Select settings, Admin sign-in, and find out what controls or screen time protection they offer. Choose the ones you wish to activate, especially for the time when adults are not at home.
Conclusion
Congratulations. You have successfully secured your child’s digital space and sanitized it. Discuss unsafe practices as a family, and make any digital rule breaches and irresponsible actions, or concerns, learning points for them. Let their takeaway be that parents will monitor and mentor them, but they too have to take ownership of their actions.


