#FactCheck: Viral AI video being shared online claiming Iran has destroyed Tel Aviv Ben Gurion Airport in an Iranian missile strike
Executive Summary:
A video circulating on Social media has claimed that Iran has launched a missile strike destroying Ben Gurion Airport in Tel Aviv. With rising tensions in geopolitics, the video quickly became popular. However, our research has detailed inspections through digital verification tools and visual analysis showed that the video is AI-generated. No incident or damage ever occurred.

Claim:
A viral video circulating on social media platforms claims to show Tel Aviv’s Ben Gurion Airport destroyed following an Iranian missile strike. The video is being shared with captions suggesting it is the last recorded visuals from the attack, with some users asserting it as evidence of escalating conflict between Iran and Israel.

Fact Check:
After looking into the video that purported to show the destruction of Tel Aviv's Ben Gurion Airport in an Iranian missile strike, we researched the topic whether the claim is accurate or not. The video depicts a damaged airport terminal, with debris and fires, but a visual analysis determined that there were a number of suspicious characteristics: asymmetrical layout, artificial-looking smoke patterns, and the absence of activity or humans—those are all typical indications of AI generation. Our research traced the origins of the video to an Instagram post, with a date of May 27, 2025, made by what seems to be a user who frequently shares AI-generated images.


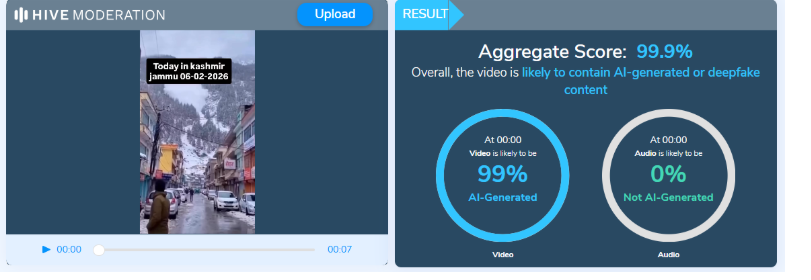
In order to verify our conclusions, we used Hive Moderation, an AI content detection tool, which produced a result of an 80% probability that the video is altered, and this level of probability strongly supports the idea that the footage is not real. Additionally, reports from popular organizations like India Today and Reuters supported these results. All findings resulting from our research established that the video is synthetic and unrelated to any event occurring at Ben Gurion Airport, and therefore debunked a false narrative propagated on social media.

To confirm, we also compared the visuals with a real aerial image of Tel Aviv’s Ben Gurion Airport available on aviation stock sites.



Fig: Google Maps image of Tel Aviv’s Ben Gurion Airport
The visuals from the viral video are not real locations or scenes of Aviv’s Ben Gurion Airport's true location and configuration therefore it is fake and misleading.
Conclusion:
After thorough research it is concluded that the viral video is fake and it is not an actual missile strike at Ben Gurion Airport. The video is made with AI, and posted by a content creator of synthetic content well before any conflict update. There is no official confirmation or credible news coverage to substantiate the claim, with a high probability of AI-detection, and it has been proven to be digitally manipulated. Therefore, the claim is untrue and misleading.
- Claim: A video shows Iran's missile strike destroying Tel Aviv’s Ben Gurion Airport.
- Claimed On: Social Media
- Fact Check: False and Misleading