#FactCheck - Viral Clip and Newspaper Article Claiming 18% GST on 'Good Morning' Messages Debunked
Executive Summary
A recent viral message on social media such as X and Facebook, claims that the Indian Government will start charging an 18% GST on "good morning" texts from April 1, 2024. This news is misinformation. The message includes a newspaper clipping and a video that was actually part of a fake news report from 2018. The newspaper article from Navbharat Times, published on March 2, 2018, was clearly intended as a joke. In addition to this, we also found a video of ABP News, originally aired on March 20, 2018, was part of a fact-checking segment that debunked the rumor of a GST on greetings.

Claims:
The claim circulating online suggests that the Government will start applying a 18% of GST on all "Good Morning" texts sent through mobile phones from 1st of April, this year. This tax would be added to the monthly mobile bills.




Fact Check:
When we received the news, we first did some relevant keyword searches regarding the news. We found a Facebook Video by ABP News titled Viral Sach: ‘Govt to impose 18% GST on sending good morning messages on WhatsApp?’

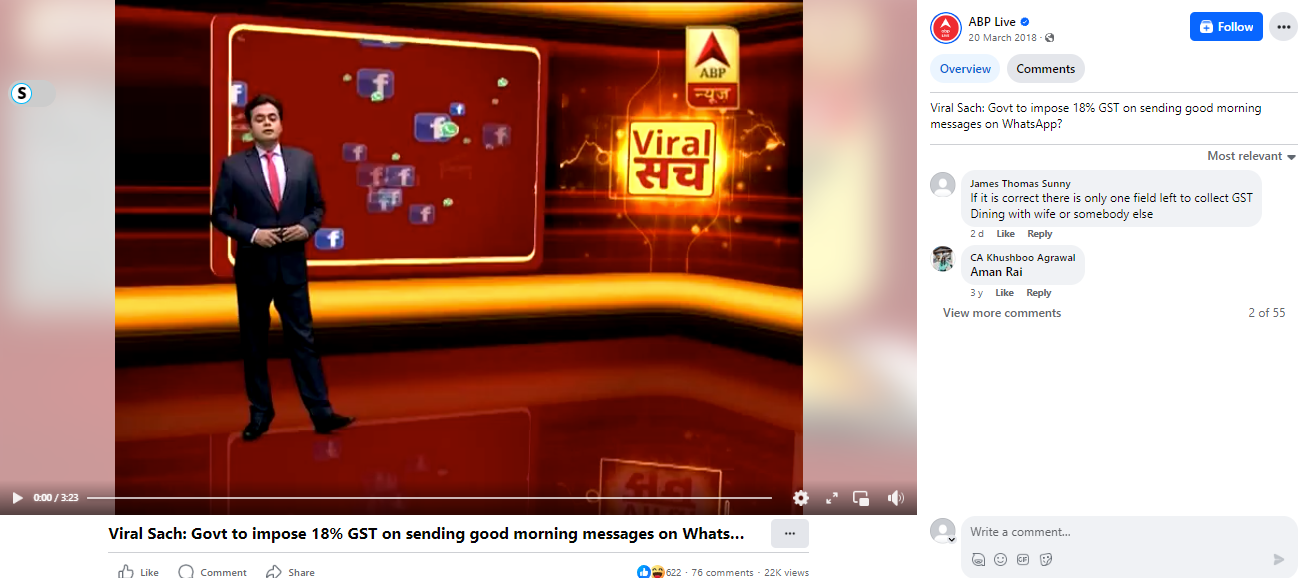
We have watched the full video and found out that the News is 6 years old. The Research Wing of CyberPeace Foundation also found the full version of the widely shared ABP News clip on its website, dated March 20, 2018. The video showed a newspaper clipping from Navbharat Times, published on March 2, 2018, which had a humorous article with the saying "Bura na mano, Holi hain." The recent viral image is a cutout image from ABP News that dates back to the year 2018.
Hence, the recent image that is spreading widely is Fake and Misleading.
Conclusion:
The viral message claiming that the government will impose GST (Goods and Services Tax) on "Good morning" messages is completely fake. The newspaper clipping used in the message is from an old comic article published by Navbharat Times, while the clip and image from ABP News have been taken out of context to spread false information.
Claim: India will introduce a Goods and Services Tax (GST) of 18% on all "good morning" messages sent through mobile phones from April 1, 2024.
Claimed on: Facebook, X
Fact Check: Fake, made as Comic article by Navbharat Times on 2 March 2018
Related Blogs

Introduction
In today’s digital world, where everything is related to data, the more data you own, the more control and compliance you have over the market, which is why companies are looking for ways to use data to improve their business. But at the same time, they have to make sure they are protecting people’s privacy. It is very tricky to strike a balance between both of them. Imagine you are trying to bake a cake where you need to use all the ingredients to make it taste great, but you also have to make sure no one can tell what’s in it. That’s kind of what companies are dealing with when it comes to data. Here, ‘Pseudonymisation’ emerges as a critical technical and legal mechanism that offers a middle ground between data anonymisation and unrestricted data processing.
Legal Framework and Regulatory Landscape
Pseudonymisation, as defined by the General Data Protection Regulation (GDPR) in Article 4(5), refers to “the processing of personal data in such a manner that the personal data can no longer be attributed to a specific data subject without the use of additional information, provided that such additional information is kept separately and is subject to technical and organisational measures to ensure that the personal data are not attributed to an identified or identifiable natural person”. This technique represents a paradigm shift in data protection strategy, enabling organisations to preserve data utility while significantly reducing privacy risks. The growing importance of this balance is evident in the proliferation of data protection laws worldwide, from GDPR in Europe to India’s Digital Personal Data Protection Act (DPDP) of 2023.
Its legal treatment varies across jurisdictions, but a convergent approach is emerging that recognises its value as a data protection safeguard while maintaining that the pseudonymised data remains personal data. Article 25(1) of GDPR recognises it as “an appropriate technical and organisational measure” and emphasises its role in reducing risks to data subjects. It protects personal data by reducing the risk of identifying individuals during data processing. The European Data Protection Board’s (EDPB) 2025 Guidelines on Pseudonymisation provide detailed guidance emphasising the importance of defining the “pseudonymisation domain”. It defines who is prevented from attributing data to specific individuals and ensures that the technical and organised measures are in place to block unauthorised linkage of pseudonymised data to the original data subjects. In India, while the DPDP Act does not explicitly define pseudonymisation, legal scholars argue that such data would still fall under the definition of personal data, as it remains potentially identifiable. The Act defines personal data defined in section 2(t) broadly as “any data about an individual who is identifiable by or in relation to such data,” suggesting that the pseudonymised information, being reversible, would continue to require compliance with data protection obligations.
Further, the DPDP Act, 2023 also includes principles of data minimisation and purpose limitation. Section 8(4) says that a “Data Fiduciary shall implement appropriate technical and organisational measures to ensure effective observance of the provisions of this Act and the Rules made under it.” The concept of Pseudonymization fits here because it is a recognised technical safeguard, which means companies can use pseudonymization as one of the methods or part of their compliance toolkit under Section 8(4) of the DPDP Act. However, its use should be assessed on a case to case basis, since ‘encryption’ is also considered one of the strongest methods for protecting personal data. The suitability of pseudonymization depends on the nature of the processing activity, the type of data involved, and the level of risk that needs to be mitigated. In practice, organisations may use pseudonymization in combination with other safeguards to strengthen overall compliance and security.
The European Court of Justice’s recent jurisprudence has introduced nuanced considerations about when pseudonymised data might not constitute personal data for certain entities. In cases where only the original controller possesses the means to re-identify individuals, third parties processing such data may not be subject to the full scope of data protection obligations, provided they cannot reasonably identify the data subjects. The “means reasonably likely” assessment represents a significant development in understanding the boundaries of data protection law.
Corporate Implementation Strategies
Companies find that pseudonymisation is not just about following rules, but it also brings real benefits. By using this technique, businesses can keep their data more secure and reduce the damage in the event of a breach. Customers feel more confident knowing that their information is protected, which builds trust. Additionally, companies can utilise this data for their research or other important purposes without compromising user privacy.
Key Benefits of Pseudonymisation:
- Enhanced Privacy Protection: It hides personal details like names or IDs with fake ones (with artificial values or codes), making it harder for accidental privacy breaches.
- Preserved Data Utility: Unlike completely anonymous data, pseudonymised data keeps its usefulness by maintaining important patterns and relationships within datasets.
- Facilitate Data Sharing: It’s easier to share pseudonymised data with partners or researchers because it protects privacy while still being useful.
However, using pseudonymisation is not as easy as companies have to deal with tricky technical issues like choosing the right methods, such as encryption or tokenisation and managing security keys safely. They have to implement strong policies to stop anyone from figuring out who the data belongs to. This can get expensive and complicated, especially when dealing with a large amount of data, and it often requires expert help and regular upkeep.
Balancing Privacy Rights and Data Utility
The primary challenge in pseudonymisation is striking the right balance between protecting individuals' privacy and maintaining the utility of the data. To get this right, companies need to consider several factors, such as why they are using the data, the potential hacker's level of skill, and the type of data being used.
Conclusion
Pseudonymisation offers a practical middle ground between full anonymisation and restricted data use, enabling organisations to harness the value of data while protecting individual privacy. Legally, it is recognised as a safeguard but still treated as personal data, requiring compliance under frameworks like GDPR and India’s DPDP Act. For companies, it is not only regulatory adherence but also ensuring that it builds trust and enhances data security. However, its effectiveness depends on robust technical methods, governance, and vigilance. Striking the right balance between privacy and data utility is crucial for sustainable, ethical, and innovation-driven data practices.
References:
- https://gdpr-info.eu/art-4-gdpr/
- https://www.meity.gov.in/static/uploads/2024/06/2bf1f0e9f04e6fb4f8fef35e82c42aa5.pdf
- https://gdpr-info.eu/art-25-gdpr/
- https://www.edpb.europa.eu/system/files/2025-01/edpb_guidelines_202501_pseudonymisation_en.pdf
- https://curia.europa.eu/juris/document/document.jsf?text=&docid=303863&pageIndex=0&doclang=EN&mode=req&dir=&occ=first&part=1&cid=16466915
- https://curia.europa.eu/juris/document/document.jsf?text=&docid=303863&pageIndex=0&doclang=EN&mode=req&dir=&occ=first&part=1&cid=16466915

Introduction
As technology advances, global connectivity becomes increasingly vital. Meta's "Project Waterworth" once completed, will reach five major continents and span over 50,000 km, making it the world’s longest subsea cable project using the highest-capacity technology available. This project is expected to bring industry-leading connectivity to the U.S., India, Brazil, South Africa, and other key regions. It will enable greater economic cooperation, facilitate digital inclusion, and open opportunities for technological development in these regions.
In India, a project such as this will help accelerate this progress and support the country’s ambitious plans for its digital economy in cohesion with the significant growth and investment in digital infrastructure that is already underway. Subsea cable projects, such as Project Waterworth, are the backbone of global digital infrastructure, accounting for more than 95% of intercontinental traffic across the world’s oceans to seamlessly enable digital communication, video experiences, online transactions, and more.
Enhancing India's Digital Infrastructure
A subsea cable, or submarine cable, enhances global internet speed and reliability by carrying massive data volumes across ocean floors, connecting countries and continents. Compared to satellites, these cables offer greater stability and minimal disruptions.
Project Waterworth aims to build the world's longest 24-fibre pair cable, improving resilience and deployment speed. The project is expected to prevent the damages in high-risk areas, through the use of innovative routing with maximising deep-water placement (up to 7,000 meters) and enhanced burial techniques. This project will play a crucial role in the advancement of AI and emerging technologies, ensuring widespread access to their benefits in India.
CyberPeace Takeaways
The said project has the potential to have manifold implications ranging from economic and policy to India-US relations, data privacy and security concerns emerging from the increase in the data flows and others. A segregated list of takeaways is as follows:
- Economic and policy implications: The project can lead to economic growth as it has the potential for job creation, and investment opportunities and can lead to positioning India as a digital hub globally. The creation of regulatory frameworks that can support and secure a large-scale infrastructure project such as this is necessary.
- India- US Relations: This project will align with the commitments that were made in the US-India joint statement on undersea technology collaboration and strengthen them. It will further serve as a model for future collaborations between the nations’ tech entities.
- Concerns for Data Privacy and Security: A robust cybersecurity mechanism which can combat the potential risks associated with the increased data flows is required. The concerned authorities need to be vigilant in monitoring and ensuring compliance with the applicable data protection standards set such as the IT Act of 2000, the DPDP Act of 2023 and its rules(once finalised).
Conclusion
India has been provided with a transformative opportunity to bolster its digital landscape by the advent of Project Waterworth. The enhancement of internet speed, stability, and capacity, will strengthen the country’s digital infrastructure and support economic growth. This project is also projected to accelerate AI-driven advancements in India. Moreover, this technological collaboration between India-US will strengthen their relations and set the stage for India to negotiate future global partnerships. A well-defined regulatory framework and strong cybersecurity measures will be crucial to proactively address data privacy, security, and governance challenges to ensure safe and equitable digital progress. As India continues its rapid digital expansion, engaging in informed discussions, policy planning, and strategic investments will be key to maximise Project Waterworth’s impact and propel India toward a more connected, innovative, and resilient digital future.
References

Introduction
Entrusted with the responsibility of leading the Global Education 2030 Agenda through the Sustainable Development Goal 4, UNESCO’s Institute for Lifelong Learning in collaboration with the Media and Information Literacy and Digital Competencies Unit has recently launched a Media and Information Literacy Course for Adult Educators. The course aligns with The Pact for The Future adopted at The United Nations Summit of the Future, September 2024 - asking for increased efforts towards media and information literacy from its member countries. The course is free for Adult Educators to access and is available until 31st May 2025.
The Course
According to a report by Statista, 67.5% of the global population uses the internet. Regardless of the age and background of the users, there is a general lack of understanding on how to spot misinformation, targeted hate, and navigating online environments in a manner that is secure and efficient. Since misinformation (largely spread online) is enabled by the lack of awareness, digital literacy becomes increasingly important. The course is designed keeping in mind that many active adult educators are yet to get an opportunity to hone their skills with regard to media and information through formal education. Self-paced, a total of 10 hours, this course covers basics such as concepts of misinformation and disinformation, artificial intelligence, and combating hate speech, and offers a certificate on completion.
CyberPeace Recommendations
As this course is free of cost, can be done in a remote capacity, and covers basics regarding digital literacy, all eligible are encouraged to take it up to familiarise themselves with such topics. However, awareness regarding the availability of this course, alongside who can avail of this opportunity can be further worked on so a larger number can avail its benefits.
CyberPeace Recommendations To Enhance Positive Impact
- Further Collaboration: As this course is open to adult educators, one can consider widening the scope through active engagement with Independent organisations and even Individual internet users who are willing to learn.
- Engagement with Educational Institutions: After launching a course, an interactive outreach programme and connecting with relevant stakeholders can prove to be beneficial. Since this course requires each individual adult educator to sign up to avail the course, partnering with educational universities, institutes, etc. is encouraged. In the Indian context, active involvement with training institutes such as DIET (District Institute of Education and Training), SCERT (State Council of Educational Research and Training), NCERT (National Council of Educational Research and Training), and Open Universities, etc. could be initiated, facilitating greater awareness and more participation.
- Engagement through NGOs: NGOs (focused on digital literacy) with a tie-up with UNESCO, can aid in implementing and encouraging awareness. A localised language approach option can be pondered upon for inclusion as well.
Conclusion
Though a long process, tackling misinformation through education is a method that deals with the issue at the source. A strong foundation in awareness and media literacy is imperative in the age of fake news, misinformation, and sensitive data being peddled online. UNESCO’s course launch garners attention as it comes from an international platform, is free of cost, truly understands the gravity of the situation, and calls for action in the field of education, encouraging others to do the same.
References
- https://www.uil.unesco.org/en/articles/media-and-information-literacy-course-adult-educators-launched
- https://www.unesco.org/en/articles/celebrating-global-media-and-information-literacy-week-2024
- https://www.unesco.org/en/node/559#:~:text=UNESCO%20believes%20that%20education%20is,must%20be%20matched%20by%20quality.


