#FactCheck: A viral claim suggests that India Post will remove all red letter boxes across the country beginning 1 September 2025.
Executive Summary:
A viral social media claim suggested that India Post would discontinue all red post boxes across the country from 1 September 2025, attributing the move to the government’s Digital India initiative. However, fact-checking revealed this claim to be false. India Post’s official X (formerly Twitter) and Instagram handles clarified on 7 August 2025 that red letterboxes remain operational, calling them timeless symbols of connection and memories. No official notice or notification regarding their discontinuation exists on the Department of Posts’ website. This indicates the viral posts were misleading and aimed at creating confusion among the public.
Claim:
A claim is circulating on social media stating that India Post will discontinue all red post boxes across the country effective 1 September 2025. According to the viral posts,[archived link] the move is being linked to the government’s push towards Digital India, suggesting that traditional post boxes have lost their relevance in the digital era.

Fact Check:
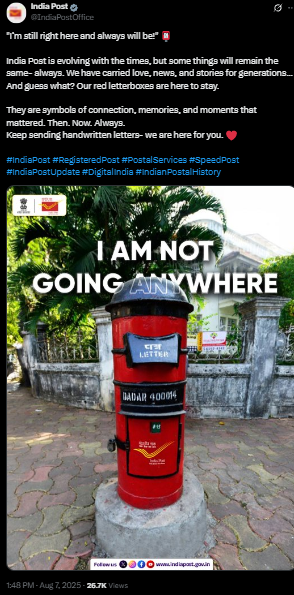
After conducting a reverse image analysis, we found that the official X handle of India Post, in a post dated 7 August 2025, clarified that the viral claim was incorrect and misleading. The post was shared with the caption:
I’m still right here and always will be!"
India Post is evolving with the times, but some things will remain the same- always. We have carried love, news, and stories for generations... And guess what? Our red letterboxes are here to stay.
They are symbols of connection, memories, and moments that mattered. Then. Now. Always.
Keep sending handwritten letters- we are here for you.
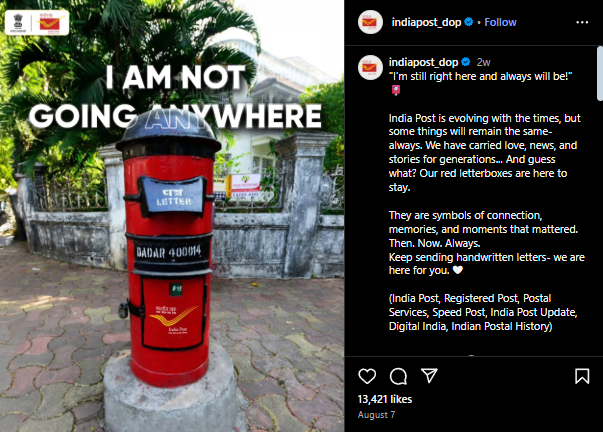
This directly refutes the viral claim about the discontinuation of the red post box from 1 September 2025. A similar clarification was also posted on the official Instagram handle @indiapost_dop on the same date.
Furthermore, after thoroughly reviewing the official website of the Department of Posts, Government of India, we found absolutely no trace, notice, or even the slightest mention of any plan to discontinue the iconic red post boxes. This complete absence of official communication strongly reinforces the fact that the viral claim is nothing more than a baseless and misleading rumour.
Conclusion:
The claim about the discontinuation of red post boxes from 1 September 2025 is false and misleading. India Post has officially confirmed that the iconic red letterboxes will continue to function as before and remain an integral part of India’s postal services.
- Claim: A viral claim suggests that India Post will remove all red letter boxes across the country beginning 1 September 2025.
- Claimed On: Social Media
- Fact Check: False and Misleading
Related Blogs
.webp)
Introduction
In the vast expanse of the digital cosmos, where the tendrils of the internet weave an intricate tapestry of connectivity, the channels through which information cascades have become a labyrinth of enigma and complexity. As we traverse this boundless virtual landscape, the line demarcating fact from fiction blurs, leaving the essence of truth adrift in a deluge of data. Amidst this ceaseless flow, platforms such as YouTube, Meta, and Twitter emerge as bulwarks in a pivotal struggle against the insidious spectres of fake news and disinformation—a struggle as fervent and consequential as any historical skirmish over the dominion of truth and influence.
Let us delve into a few case studies that illustrate the multifaceted nature of this digital warfare, where the stakes are nothing less than the integrity of public discourse and the sanctity of societal harmony.
Case 1: A Chief Minister's Stand Against Digital Deception
In the northeastern reaches of India, Assam's Chief Minister, Himanta Biswa Sarma, confronted disinformation head-on. With the spectre of elections looming like a storm on the horizon, he took to the microblogging site X to unveil a nefarious scheme—a doctored video intended to distort his speech and sow seeds of communal discord. 'See for yourself, as elections approach, how vested groups distort a speech with the criminal intention of spreading disinformation and communal disharmony. The long arms of the law will catch up with these elements,' declared Sarma, his words a clarion call for vigilance.
The counterfeit video, crafted to smear the Chief Minister's reputation, elicited a swift and decisive response from Assam's Director General of Police, G.P. Singh. 'Noted Sir. CID Assam would register a criminal case and investigate the people behind this,' assured Singh, signalling the readiness of the law to pursue the purveyors of falsehood.
Case 2: Waves of Deceit: Unverified Claims of Cancellations in the Maldives Tourism Controversy
The narrative shifts to the idyllic archipelago of the Maldives, where the azure waters belie a tumultuous undercurrent of diplomatic discord with India. Following disparaging remarks by Maldivian officials directed at Indian Prime Minister Narendra Modi, the social media sphere became rife with claims of Indian tourists en masse cancelling their sojourns to the island nation. Screenshots purporting to show cancelled bookings flooded platforms like X, with one user claiming to have annulled a reservation at the Palms Retreat, Fulhadhoo, to the tune of at least Rs 5 lakh, citing the officials' 'racist remarks.'
Initial reports from a few media outlets lent credence to this narrative of widespread cancellations. However, upon closer scrutiny, the veracity of these claims crumbled like a sandcastle at high tide. Concrete evidence to substantiate the alleged boycott was conspicuously absent, and neither travel agencies nor airlines corroborated the supposed trend.
The controversy was inflamed when PM Modi's visit to Lakshadweep, and subsequent social media posts praising the archipelago, spurred Indian users to champion Lakshadweep as an alternative to the Maldives. The vitriolic response from Maldivian ministers, who labelled Modi with derogatory remarks, ignited a firestorm on X, with hashtags like #BoycottMaldives and #MaldivesBoycott trending fervently.
Yet, the truth behind the cacophony of cancellation numbers remains shrouded in ambiguity, with no official acknowledgement from either government and a conspicuous absence of data from the tourism industry.
Case 3: Misinformation Highway: Unraveling the Fabrications in Bollywood's rumours or misinformation: Lies, Thumbnails, and Digital Dalliances
Gaze now turns to the bustling fabricated thumbnails or rumour taglines on uploaded videos on YouTube, where thumbnails emblazoned with tantalising texts beckon viewers with the promise of scandalous revelations. 'Pregnant? Divorced?' they shout, luring millions into their web with the allure of salacious 'news.' Yet, these are but mirages, baseless rumours masquerading as fact, or worse, complete fabrications.
The platform teems with counterfeit narratives and rumours, targeting the luminaries of Bollywood. Factors such as easy content uploading without strict scrutiny, a burgeoning digital footprint, and India's insatiable appetite for celebrity culture have created a fertile ground for the proliferation of such content. It is a testament to the power of the digital age, where anyone with a connection can craft a narrative and cast it into the ether, regardless of its foundation in reality.
We must arm ourselves with discernment and scepticism in this relentless onslaught of misinformation. The digital realm, for all its wonders, is also a battleground where the currency is truth, and the price of negligence is the erosion of our collective understanding. As we navigate this ever-evolving landscape, let us hold fast to the principles of verification and evidence, for they are the compass by which we can chart a course through the maelstrom of misinformation that seeks to engulf us.
Conclusion
In this era of digital enlightenment, it is incumbent upon us to discern the chaff from the wheat, to elevate the discourse beyond the mire of falsehoods. Let us endeavour to foster a digital polity that values truth, champions authenticity, and resolutely stands against the tide of disinformation that threatens to undermine the very fabric of our society.
References:
- https://www.indiatodayne.in/assam/video/assam-cm-exposes-fake-video-scheme-dgp-promises-swift-action-743097-2024-01-08
- https://www.thequint.com/news/webqoof/boycott-maldives-misinformation-on-trip-booking-cancellations
- https://www.thequint.com/news/webqoof/bollywood-fake-news-on-youtube-uses-divorce-pregnancy-and-arrests-for-misinformation

Introduction
As the sun rises on a new chapter in the Indian telecommunications narrative, the corridors of power in New Delhi are abuzz with palpable excitement and a hint of solemnity. Here, a groundbreaking proposal stands before the lawmakers of the Lok Sabha, not simply a proposed amendment or update to an existing statute, but the cornerstone of a reimagined communications epoch—the Telecommunications Bill of 2023. In every sense, this legislative masterpiece embodies a country at the intersection of tradition and innovation, eager to part ways with vestiges of colonial infrastructure that have shaped its modern landscape.
The Origins
Steeped in history, India's telecommunications system has persevered through a patchwork of regulations and ad hoc policies, growing somewhat unwieldy under the shadow of the Indian Telegraph Act (1885), the Wireless Telegraphy Act (1933), and the Telegraph Wires (Unlawful Possession) Act (1950). Yet, it is within this context of the old guard, a relic of British administration, that the new Telecommunications Bill seeks to transcend the limitations of the past. It aims to dismantle barriers and create an ecosystem that is fluid, adaptable, and resonant with the rapid cadence of technological advancements and the demands of a population increasingly reliant on digital connectivity.
In crafting this bill, the creators have meticulously knitted together an intricate fabric of vibrant threads, each signifying a pillar of progress. To herald an era of unparalleled growth and dynamism, the bill looks beyond the scope of traditional telecommunication services, boldly embracing the convergence of digital mediums such as wire, radio, and optical fibers, aligning with the modalities of 21st-century communication. The bill’s very essence is innovation, etching a new paradigm through its provisions and signalling India's readiness to interface with the ever-expanding digital frontier.
The Defining Features
A novel and defining feature of this bill is its departure from a rigid licensing regime. It forges ahead with 'authorizations'—a signifier that resonates with flexibility, adaptability, and a regulatory approach that isn't mired in bureaucratic inertia but is rather an enabler of swift technological adoption and market responsiveness. This transformative philosophy signifies a departure from the byzantine processes of yore, orbiting instead toward an agile governance model that is both responsive to current needs and anticipative of future trends.
The introduction of mandatory biometric authentication for telecom customers articulates an unyielding stance against the rampant misuse of communication networks. Indeed, this measure draws a fine line between the right to privacy and the exigencies of data protection, posing ethical questions that animate public discourse. This balance seeks to thwart unsolicited commercial communication, exemplifying the state's vigil on the sanctuaries of personal space and tranquility.
In addition, the forward-looking bill tactically addresses the strategic use of spectrum resources with an undercurrent of prescience. By granting ‘spectrum assets’ legislative stature through the National Frequency Allocation Plan and enabling operators to adapt through 'refarming', the bill forms a visionary blueprint for resource optimization. It inherently recognizes that bandwidth is not simply a commercial commodity but one that serves the wider canvas of national imperatives, connectivity goals, and developmental aspirations.
Further embodying the dual themes of openness and vigilance, the bill incorporates provisions for interception and the implementation of a 'trusted sources' regime, a tacit acknowledgement of the cybersecurity challenges that loom on the horizon amidst increasing geopolitical strains. These measures exemplify the act of walking a tightrope between the democratic ideals of transparency and the unyielding requirements of state security.
Looking to the skies, the bill embraces satellite technologies, foreseeing their potential in unshackling the remote and marginalized areas from the constraints of terrestrial infrastructure and thus forging a digitally inclusive society. Acknowledging the expanse of the Indian subcontinent, the bill paves the way for an interconnected, digital hinterland via thoughtful satellite spectrum allocations.
Emphasizing the human thread in the digital weave, the reformulation of the Universal Service Obligation Fund into 'Digital Bharat Nidhi' underscores an unwavering commitment to reaching the unreached. It's the crystallization of a promise that every Indian, regardless of geographical and socio-economic divides, will be privy to the lenses of opportunity presented by the digital revolution.
The Watershed Moment
The introduction of the Telecommunications Bill of 2023 is a watershed moment, a convergence where history and opportunity coalesce, propelling a nation forward with the ambitions of a burgeoning superpower replacing the Indian Telegraph Act (1885), the Wireless Telegraphy Act (1933), and the Telegraph Wires (Unlawful Possession) Act (1950). It carries within its articles and clauses the anticipation of a billion dreams, the catalyst to a regulatory environment that nurtures innovation, equality, and a forward leap into the future.
Conclusion
Through its comprehensive scope and visionary approach, the bill writes a fresh chapter in India's digital saga. It is an unfolding story, pregnant with the possibilities of a nascent digital age, charting a trajectory for an India poised to define its own digital dome of the sky, under which its citizens will thrive for generations to come. With every legislative step, India crafts its legacy, a narrative of evolution, a tableau that reflects the aspirations of its people and their resolve to embrace the force of technology for the collective good. As this bill advances through the legislative labyrinth, it carries the spirit of a digital renaissance nestled in the heart of the world's largest democracy.
References

Introduction
The Ministry of Electronics and Information Technology recently released the IT Intermediary Guidelines 2023 Amendment for social media and online gaming. The notification is crucial when the Digital India Bill’s drafting is underway. There is no denying that this bill, part of a series of bills focused on amendments and adding new provisions, will significantly improve the dynamics of Cyberspace in India in terms of reporting, grievance redressal, accountability and protection of digital rights and duties.
What is the Amendment?
The amendment comes as a key feature of cyberspace as the bill introduces fact-checking, a crucial aspect of relating information on various platforms prevailing in cyberspace. Misformation and disinformation were seen rising significantly during the Covid-19 pandemic, and fact-checking was more important than ever. This has been taken into consideration by the policymakers and hence has been incorporated as part of the Intermediary guidelines. The key features of the guidelines are as follows –
- The phrase “online game,” which is now defined as “a game that is offered on the Internet and is accessible by a user through a computer resource or an intermediary,” has been added.
- A clause has been added that emphasises that if an online game poses a risk of harm to the user, intermediaries and complaint-handling systems must advise the user not to host, display, upload, modify, publish, transmit, store, update, or share any data related to that risky online game.
- A proviso to Rule 3(1)(f) has been added, which states that if an online gaming intermediary has provided users access to any legal online real money game, it must promptly notify its users of the change, within 24 hours.
- Sub-rules have been added to Rule 4 that focus on any legal online real money game and require large social media intermediaries to exercise further due diligence. In certain situations, online gaming intermediaries:
- Are required to display a demonstrable and obvious mark of verification of such online game by an online gaming self-regulatory organisation on such permitted online real money game
- Will not offer to finance themselves or allow financing to be provided by a third party.
- Verification of real money online gaming has been added to Rule 4-A.
- The Ministry may name as many self-regulatory organisations for online gaming as it deems necessary for confirming an online real-money game.
- Each online gaming self-regulatory body will prominently publish on its website/mobile application the procedure for filing complaints and the appropriate contact information.
- After reviewing an application, the self-regulatory authority may declare a real money online game to be a legal game if it is satisfied that:
- There is no wagering on the outcome of the game.
- Complies with the regulations governing the legal age at which a person can engage into a contract.
- The Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021 have a new rule 4-B (Applicability of certain obligations after an initial period) that states that the obligations of the rule under rules 3 and 4 will only apply to online games after a three-month period has passed.
- According to Rule 4-C (Obligations in Relation to Online Games Other Than Online Real Money Games), the Central Government may direct the intermediary to make necessary modifications without affecting the main idea if it deems it necessary in the interest of India’s sovereignty and integrity, the security of the State, or friendship with foreign States.
- Intermediaries, such as social media companies or internet service providers, will have to take action against such content identified by this unit or risk losing their “safe harbour” protections under Section 79 of the IT Act, which let intermediaries escape liability for what third parties post on their websites. This is problematic and unacceptable. Additionally, these notified revisions can circumvent the takedown order process described in Section 69A of the IT Act, 2000. They also violated the ruling in Shreya Singhal v. Union of India (2015), which established precise rules for content banning.
- The government cannot decide if any material is “fake” or “false” without a right of appeal or the ability for judicial monitoring since the power to do so could be abused to thwart examination or investigation by media groups. Government takedown orders have been issued for critical remarks or opinions posted on social media sites; most of the platforms have to abide by them, and just a few, like Twitter, have challenged them in court.
Conclusion
The new rules briefly cover the aspects of fact-checking, content takedown by Govt, and the relevance and scope of sections 69A and 79 of the Information Technology Act, 2000. Hence, it is pertinent that the intermediaries maintain compliance with rules to ensure that the regulations are sustainable and efficient for the future. Despite these rules, the responsibility of the netizens cannot be neglected, and hence active civic participation coupled with such efficient regulations will go a long way in safeguarding the Indian cyber ecosystem.


