#FactCheck – False Claim of Lord Ram's Hologram in Srinagar - Video Actually from Dehradun
Executive Summary:
A video purporting to be from Lal Chowk in Srinagar, which features Lord Ram's hologram on a clock tower, has gone popular on the internet. The footage is from Dehradun, Uttarakhand, not Jammu and Kashmir, the CyberPeace Research Team discovered.
Claims:
A Viral 48-second clip is getting shared over the Internet mostly in X and Facebook, The Video shows a car passing by the clock tower with the picture of Lord Ram. A screen showcasing songs about Lord Ram is shown when the car goes forward and to the side of the road.

The Claim is that the Video is from Kashmir, Srinagar

Similar Post:

Fact Check:
The CyberPeace Research team found that the Information is false. Firstly we did some keyword search relating to the Caption and found that the Clock Tower in Srinagar is not similar to the Video.

We found an article by NDTV mentioning Srinagar Lal Chowk’s Clock Tower, It's the only Clock Tower in the Middle of Road. We are somewhat confirmed that the Video is not From Srinagar. We then ran a reverse image search of the Video by breaking down into frames.
We found another Video that visualizes a similar structure tower in Dehradun.

Taking a cue from this we then Searched for the Tower in Dehradun and tried to see if it matches with the Video, and yes it’s confirmed that the Tower is a Clock Tower in Paltan Bazar, Dehradun and the Video is actually From Dehradun but not from Srinagar.
Conclusion:
After a thorough Fact Check Investigation of the Video and the originality of the Video, we found that the Visualisation of Lord Ram in the Clock Tower is not from Srinagar but from Dehradun. Internet users who claim the Visual of Lord Ram from Srinagar is totally Baseless and Misinformation.
- Claim: The Hologram of Lord Ram on the Clock Tower of Lal Chowk, Srinagar
- Claimed on: Facebook, X
- Fact Check: Fake
Related Blogs

Introduction
Artificial Intelligence (AI) is fast transforming our future in the digital world, transforming healthcare, finance, education, and cybersecurity. But alongside this technology, bad actors are also weaponising it. More and more, state-sponsored cyber actors are misusing AI tools such as ChatGPT and other generative models to automate disinformation, enable cyberattacks, and speed up social engineering operations. This write-up explores why and how AI, in the form of large language models (LLMs), is being exploited in cyber operations associated with adversarial states, and the necessity for international vigilance, regulation, and AI safety guidelines.
The Shift: AI as a Cyber Weapon
State-sponsored threat actors are misusing tools such as ChatGPT to turbocharge their cyber arsenal.
- Phishing Campaigns using AI- Generative AI allows for highly convincing and grammatically correct phishing emails. Unlike the shoddily written scams of yesteryears, these AI-based messages are tailored according to the victim's location, language, and professional background, increasing the attack success rate considerably. Example: It has recently been reported by OpenAI and Microsoft that Russian and North Korean APTs have employed LLMs to create customised phishing baits and malware obfuscation notes.
- Malware Obfuscation and Script Generation- Big Language Models (LLMs) such as ChatGPT may be used by cyber attackers to help write, debug, and camouflage malicious scripts. While the majority of AI instruments contain safety mechanisms to guard against abuse, threat actors often exploit "jailbreaking" to evade these protections. Once such constraints are lifted, the model can be utilised to develop polymorphic malware that alters its code composition to avoid detection. It can also be used to obfuscate PowerShell or Python scripts to render them difficult for conventional antivirus software to identify. Also, LLMs have been employed to propose techniques for backdoor installation, additional facilitating stealthy access to hijacked systems.
- Disinformation and Narrative Manipulation
State-sponsored cyber actors are increasingly employing AI to scale up and automate disinformation operations, especially on election, protest, and geopolitical dispute days. With LLMs' assistance, these actors can create massive amounts of ersatz news stories, deepfake interview transcripts, imitation social media posts, and bogus public remarks on online forums and petitions. The localisation of content makes this strategy especially perilous, as messages are written with cultural and linguistic specificity, making them credible and more difficult to detect. The ultimate aim is to seed societal unrest, manipulate public sentiments, and erode faith in democratic institutions.
Disrupting Malicious Uses of AI – OpenAI Report (June 2025)
OpenAI released a comprehensive threat intelligence report called "Disrupting Malicious Uses of AI" and the “Staying ahead of threat actors in the age of AI”, which outlined how state-affiliated actors had been testing and misusing its language models for malicious intent. The report named few advanced persistent threat (APT) groups, each attributed to particular nation-states. OpenAI highlighted that the threat actors used the models mostly for enhancing linguistic quality, generating social engineering content, and expanding operations. Significantly, the report mentioned that the tools were not utilized to produce malware, but rather to support preparatory and communicative phases of larger cyber operations.
AI Jailbreaking: Dodging Safety Measures
One of the largest worries is how malicious users can "jailbreak" AI models, misleading them into generating banned content using adversarial input. Some methods employed are:
- Roleplay: Simulating the AI being a professional criminal advisor
- Obfuscation: Concealing requests with code or jargon
- Language Switching: Proposing sensitive inquiries in less frequently moderated languages
- Prompt Injection: Lacing dangerous requests within innocent-appearing questions
These methods have enabled attackers to bypass moderation tools, transforming otherwise moral tools into cybercrime instruments.
Conclusion
As AI generations evolve and become more accessible, its application by state-sponsored cyber actors is unprecedentedly threatening global cybersecurity. The distinction between nation-state intelligence collection and cybercrime is eroding, with AI serving as a multiplier of adversarial campaigns. AI tools such as ChatGPT, which were created for benevolent purposes, can be targeted to multiply phishing, propaganda, and social engineering attacks. The cross-border governance, ethical development practices, and cyber hygiene practices need to be encouraged. AI needs to be shaped not only by innovation but by responsibility.
References
- https://www.microsoft.com/en-us/security/blog/2024/02/14/staying-ahead-of-threat-actors-in-the-age-of-ai/
- https://www.bankinfosecurity.com/openais-chatgpt-hit-nation-state-hackers-a-28640
- https://oecd.ai/en/incidents/2025-06-13-b5e9
- https://www.microsoft.com/en-us/security/security-insider/meet-the-experts/emerging-AI-tactics-in-use-by-threat-actors
- https://www.wired.com/story/youre-not-ready-for-ai-hacker-agents/
- https://www.cert-in.org.in/PDF/Digital_Threat_Report_2024.pdf
- https://cdn.openai.com/threat-intelligence-reports/5f73af09-a3a3-4a55-992e-069237681620/disrupting-malicious-uses-of-ai-june-2025.pdf

Introduction
Earlier this month, lawmakers in Colorado, a U.S. state, were summoned to a special legislative session to rewrite their newly passed Artificial Intelligence (AI) law before it even takes effect. Although the discussion taking place in Denver may seem distant, evolving regulations like this one directly address issues that India will soon encounter as we forge our own course for AI governance.
The Colorado Artificial Intelligence Act
Colorado became the first U.S. state to pass a comprehensive AI accountability law, set to come into force in 2026. It aims to protect people from bias, discrimination, and harm caused by predictive algorithms since AI tools have been known to reproduce societal biases by sidelining women from hiring processes, penalising loan applicants from poor neighbourhoods, or through welfare systems that wrongly deny citizens their benefits. But the law met resistance from tech companies who threatened to pull out form the state, claiming it is too broad in scope in its current form and would stifle innovation. This brings critical questions about AI regulation to the forefront:
- Who should be responsible when AI causes harm? Developers, deployers, or both?
- How should citizens seek justice?
- How can tech companies be incentivised to develop safe technologies?
Colorado’s governor has called a special session to update the law before it kicks in.
What This Means for India
India is on its path towards framing a dedicated AI-specific law or directions, and discussions are underway through the IndiaAI Mission, the proposed Digital India Act, committee set by the Delhi High Court on deepfake and other measures. But the dilemmas Colorado is wrestling with are also relevant here.
- AI uptake is growing in public service delivery in India. Facial recognition systems are expanding in policing, despite accuracy and privacy concerns. Fintech apps using AI-driven credit scoring raise questions of fairness and transparency.
- Accountability is unclear. If an Indian AI-powered health app gives faulty advice, who should be liable- the global developer, the Indian startup deploying it, or the regulator who failed to set safeguards?
- India has more than 1,500 AI startups (NASSCOM), which, like Colorado’s firms, fear that onerous compliance could choke growth. But weak guardrails could undermine public trust in AI altogether.
Lessons for India
India’s Ministry of Electronics and IT ( MEITy) favours a light-touch approach to AI regulation, and exploring and advancing ways for a future-proof guideline. Further, lessons from other global frameworks can guide its way.
- Colorado’s case shows us the necessity of incorporating feedback loops in the policy-making process. India should utilise regulatory sandboxes and open, transparent consultation processes before locking in rigid rules.
- It will also need to explore proportionate obligations, lighter for low-risk applications and stricter for high-risk use cases such as policing, healthcare, or welfare delivery.
- Europe’s AI Act is heavy on compliance, the U.S. federal government leans toward deregulation, and Colorado is somewhere in between. India has the chance to create a middle path, grounded in our democratic and developmental context.
Conclusion
As AI becomes increasingly embedded in hiring, banking, education, and welfare, opportunities for ordinary Indians are being redefined. To shape how this pans out, states like Tamil Nadu and Telangana have taken early steps to frame AI policies. Lessons will emerge from their initiative in addressing AI governance. Policy and regulation will always be contested, but contestations are a part of the process.
The Colorado debate shows us how participative law-making, with room for debate, revision, and iteration, is not a weakness but a necessity. For India’s emerging AI governance landscape, the challenge will be to embrace this process while ensuring that citizen rights and inclusion are balanced well with industry concerns. CyberPeace advocates for responsible AI regulation that balances innovation and accountability.
References
- https://www.cbsnews.com/colorado/news/colorado-lawmakers-look-repeal-replace-controversial-artificial-intelligence-law/
- https://www.naag.org/attorney-general-journal/a-deep-dive-into-colorados-artificial-intelligence-act/
- https://carnegieendowment.org/research/2024/11/indias-advance-on-ai-regulation?lang=en
- https://the-captable.com/2024/12/india-ai-regulation-light-touch/
- https://indiaai.gov.in/article/tamilnadu-s-ai-policy-six-step-tamdef-guidance-framework-and-deepmax-scorecard
Executive Summary
A video circulating on social media shows a woman using abusive language in front of a camera. Users sharing the clip claim that the woman is a professor at Galgotias University and that the video exposes her alleged reality. However, an research by CyberPeace found the claim to be misleading. The probe revealed that the woman seen in the viral video has no connection with Galgotias University and is not a professor there.Fact-checking further showed that the video is not recent but around seven years old. The woman featured in the clip was identified as Shubhrastha, who is a political strategist by profession.
Claim:
A user on X (formerly Twitter) shared the viral video on February 18, 2026, claiming: “A ‘class in abuse studies’ at Galgotias University? An obscene video of a professor teaching ethics has gone viral. Another shameful chapter has been added to the list of controversies surrounding Galgotias University.” The post further alleged that after falsely claiming a Chinese robot as its own, the university’s “Culture and Ethics” faculty member was seen publicly using abusive language in the viral clip. The post link and its archived version are provided below:
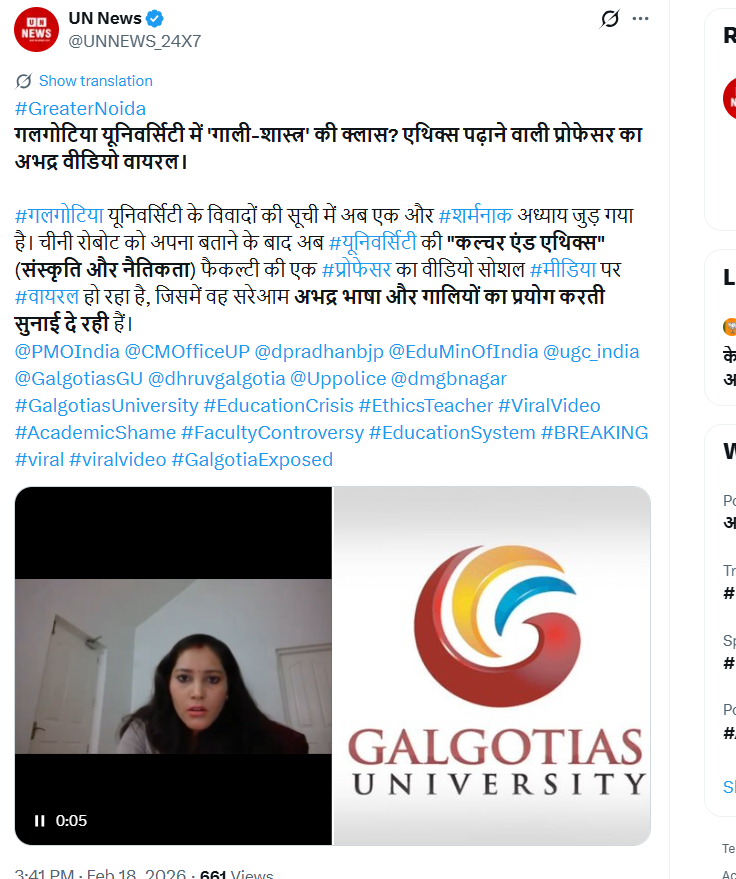
Fact Check:
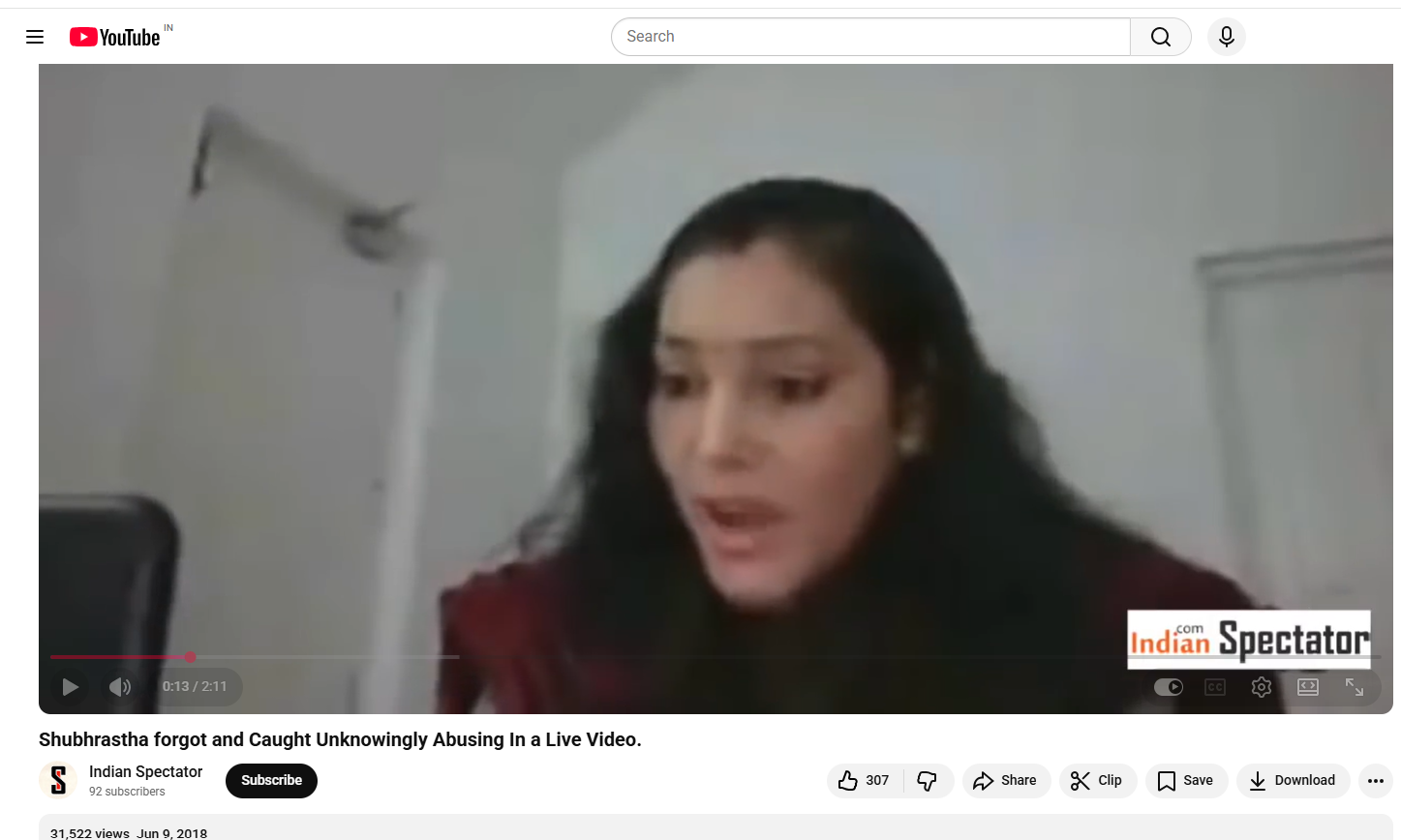
To verify the authenticity of the viral claim, we extracted key frames from the video and conducted a reverse image search using Google Lens. During the research , we found the same video uploaded on the Indian Spectator’s YouTube channel on June 9, 2018
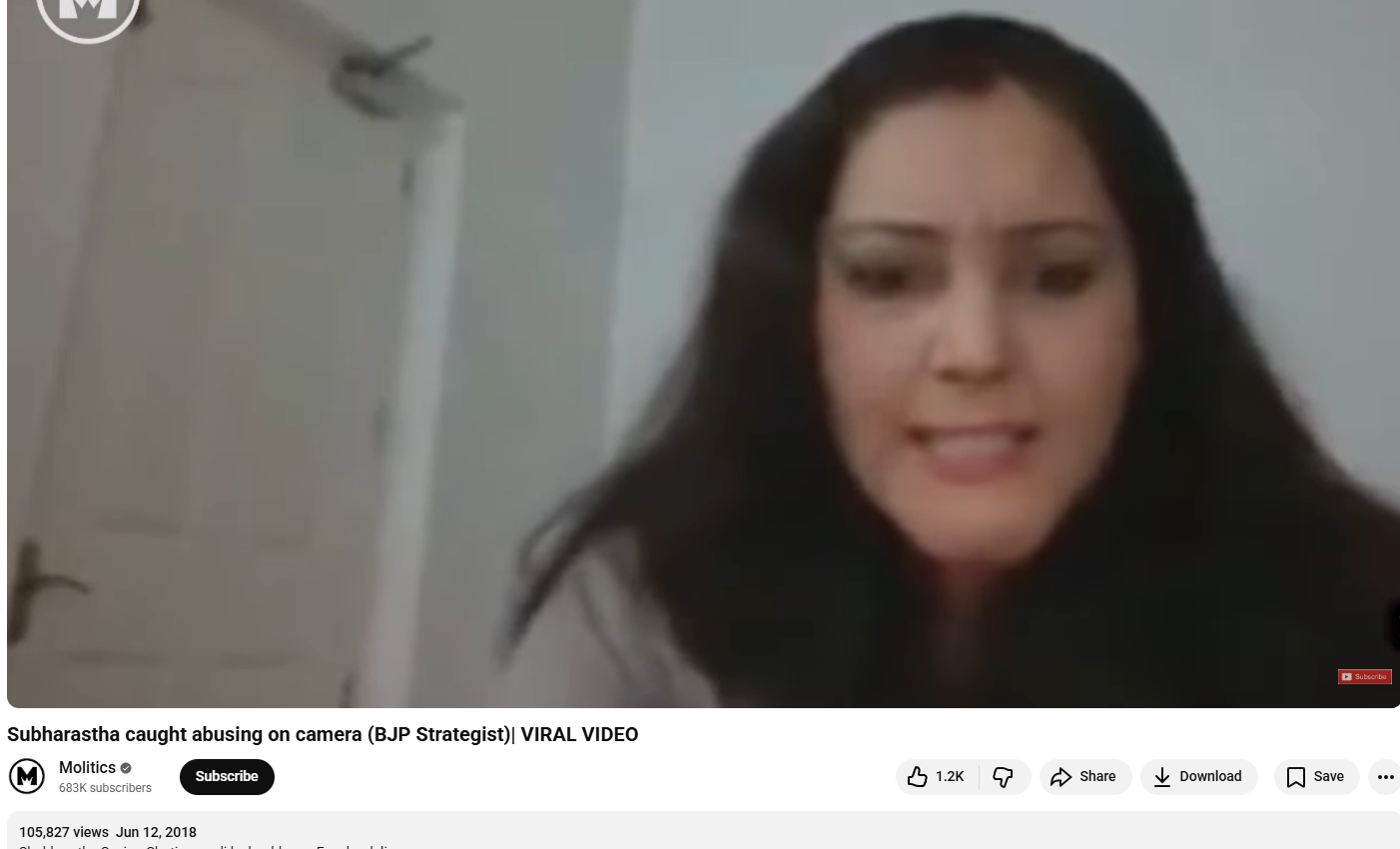
The video was also found on another YouTube channel, where it had been uploaded on June 12, 2018.
Conclusion
The research clearly establishes that the woman seen in the viral video has no association with Galgotias University and is not a professor there. The clip is also not recent but approximately seven years old. The woman in the video was identified as Shubhrastha, a political strategist.


