#FactCheck – Human Helicopter or AI Illusion? The Truth Behind the Viral Flying Man Video
Executive Summary:
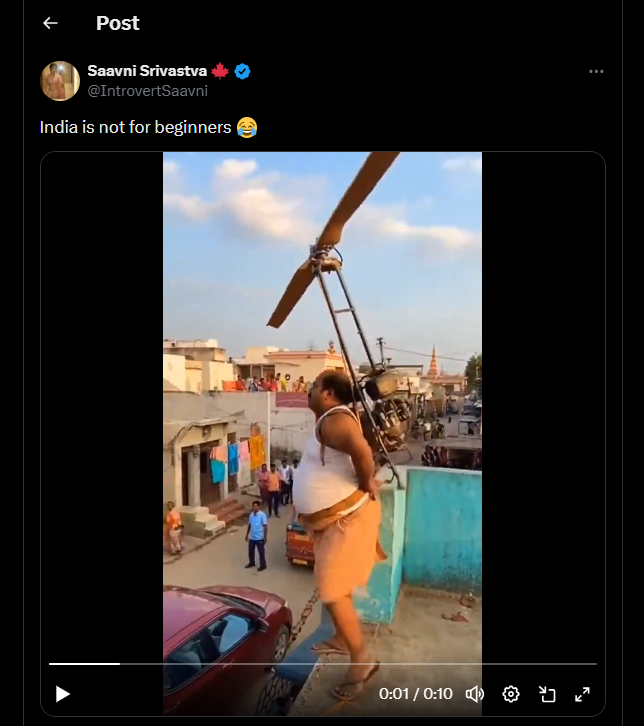
A viral video circulating on social media shows a man attempting to fly using a helicopter like fan attached to his body, followed by a crash onto a parked car. The clip was widely shared with humorous captions, suggesting it depicts a real life incident. Given the unusual nature of the visuals, the video was subjected to technical verification using AI content detection tools. Analysis using the AI detection platform indicates that the video is AI generated, and not a genuine real world event.
Claim:
A viral video (archive link) claims to show a person attempting to fly using a self made helicopter fan mechanism, briefly lifting off before crashing onto a car in a public setting. The video shows a man attempting to fly by strapping a helicopter like rotating fan to himself, essentially trying to imitate a human helicopter using a DIY mechanism. For a brief moment, it appears as if the device might work, but the attempt quickly fails due to lack of control, engineering support, and safety measures. Within seconds, the man loses balance and crashes down, landing on top of a parked car. The scene highlights a mix of overconfidence, unregulated experimentation, and risk taking carried out in a public space, with bystanders watching rather than intervening. The clip is shared humorously with the caption “India is not for beginners”.
Fact Check:
To verify the authenticity of the video, it was analyzed using the Hive Moderation AI detection tool, a widely used platform for identifying synthetic and AI generated media. The tool flagged the video with a high probability of AI generation, indicating that the visuals are not captured from a real physical event. Additional indicators such as unrealistic motion physics, inconsistent human object interaction further support the conclusion that the clip was artificially generated or heavily manipulated using generative AI techniques. No credible news reports or independent eyewitness sources corroborate the occurrence of such an incident.
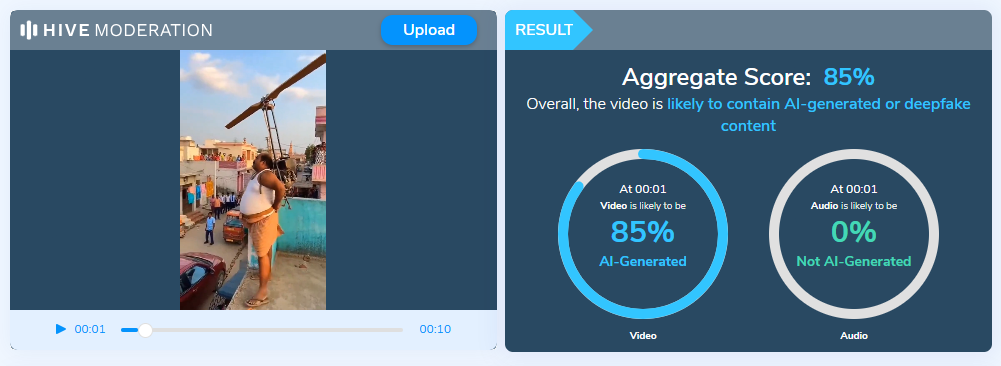
Conclusion:
The claim that the video shows an individual attempting and failing to fly using a helicopter like device is false. Technical analysis confirms that the video is AI generated, and it should be treated as synthetic or fictional content rather than a real life incident. This case highlights how AI generated videos, when shared without context, can mislead audiences and be mistaken for real events, reinforcing the need for verification tools and critical evaluation of viral content.
- Claim: A viral video claims to show a person attempting to fly using a self made helicopter fan mechanism, briefly lifting off before crashing onto a car in a public setting
- Claimed On: X (Formally Twitter)
- Fact Check: False and Misleading