#Fact Check: Viral Footage from Bangladesh Incorrectly Portrayed as Immigrant March for Violence in Assam.
Executive Summary:
As we researched a viral social media video we encountered, we did a comprehensive fact check utilizing reverse image search. The video circulated with the claim that it shows illegal Bangladeshi in Assam's Goalpara district carrying homemade spears and attacking a police and/or government official. Our findings are certain that this claim is false. This video was filmed in the Kishoreganj district, Bangladesh, on July 1, 2025, during a political argument involving two rival factions of the Bangladesh Nationalist Party (BNP). The footage has been intentionally misrepresented, putting the report into context regarding Assam to disseminate false information.

Claim:
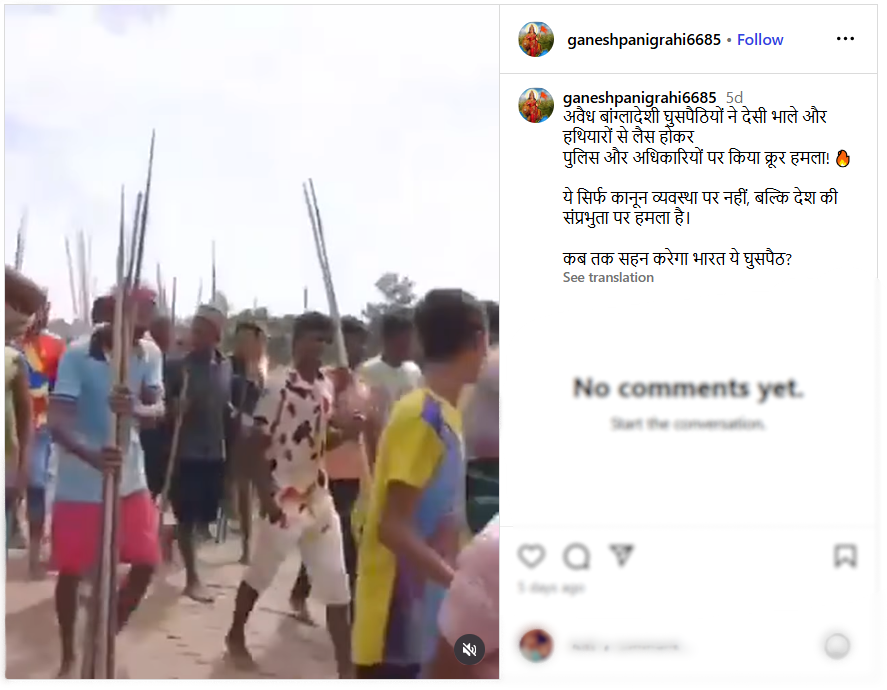
The viral video shows illegal Bangladeshi immigrants armed with spears marching in Goalpara, Assam, with the intention of attacking police or officials.
Fact Check:
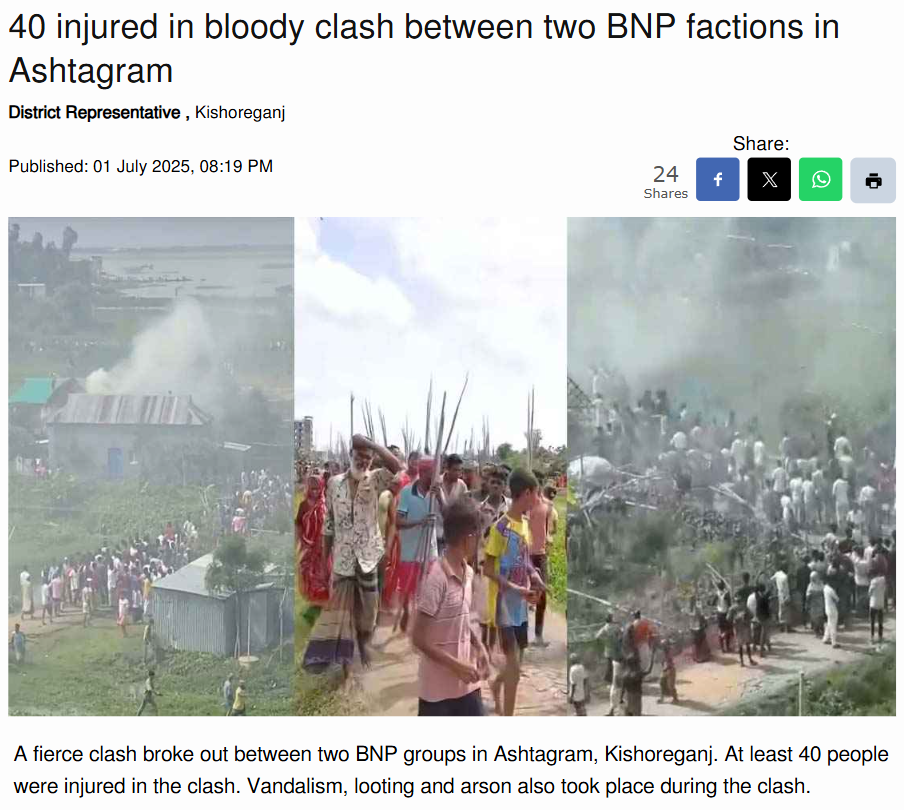
To establish if the claim was valid, we performed a reverse image search on some of the key frames from the video. We did our research on a number of news articles and social media posts from Bangladeshi sources. This led us to a reality check as the events confirmed in these reports took place in Ashtagram, Kishoreganj district, Bangladesh, in a violent political confrontation between factions of the Bangladesh Nationalist Party (BNP) on July 1, 2025, that ultimately resulted in about 40 injuries.
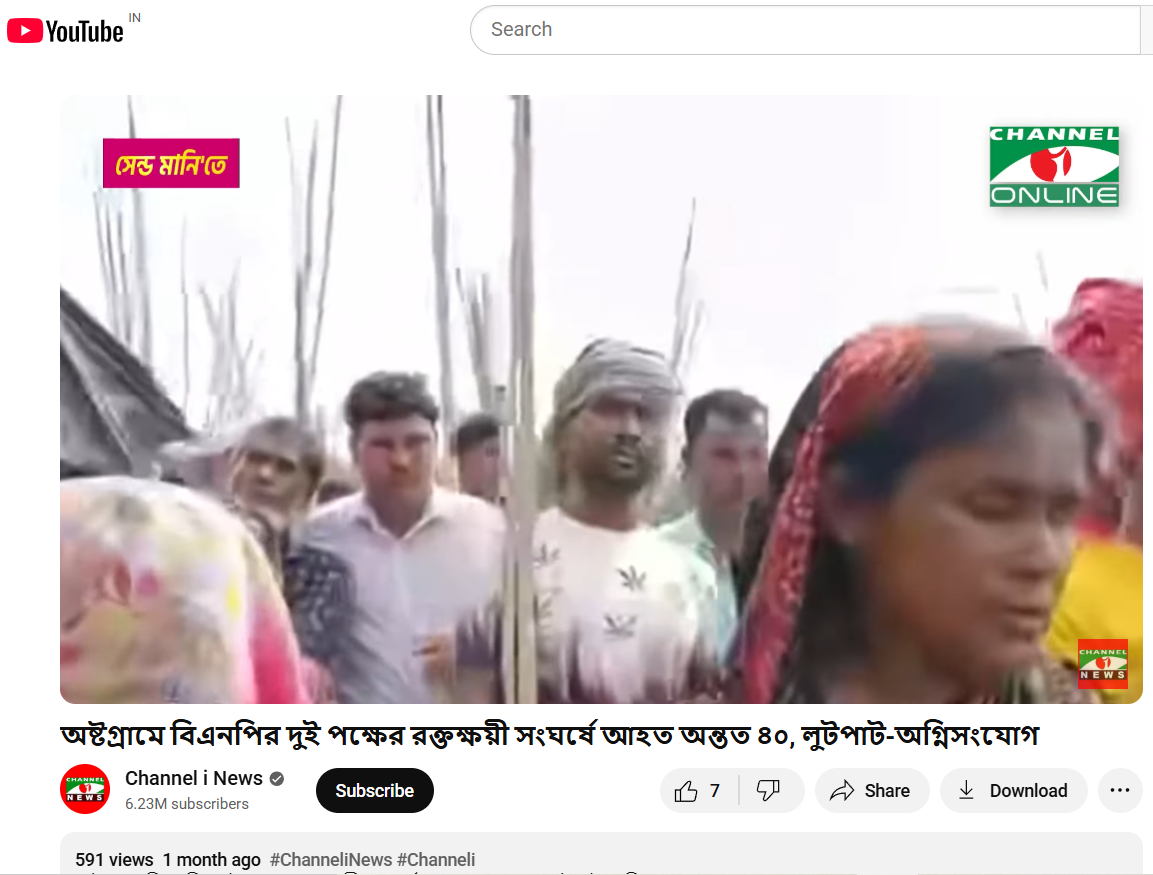
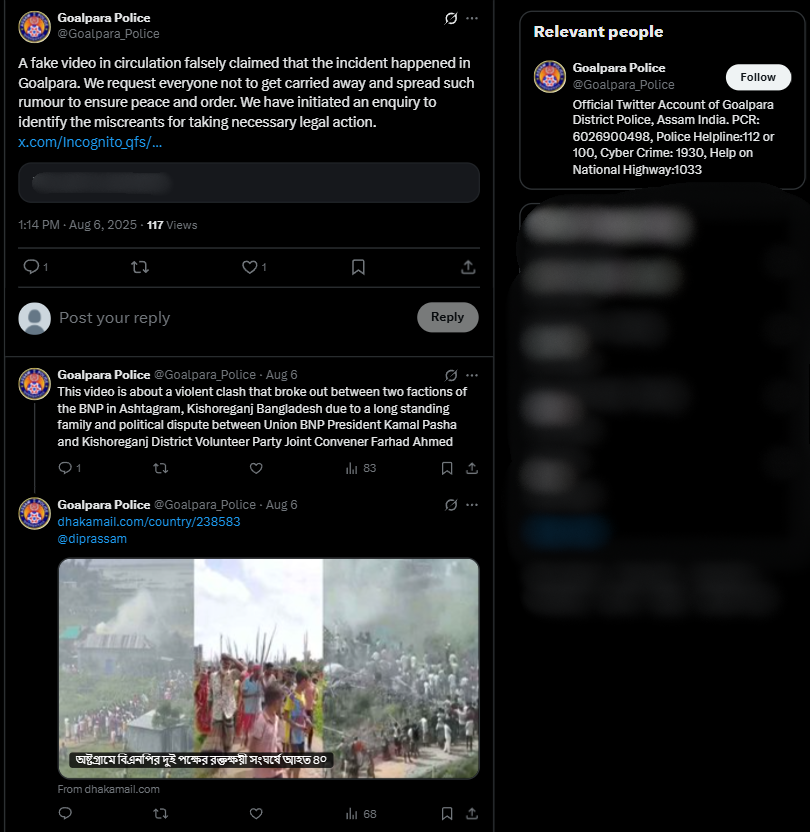
We also found on local media, in particular, Channel i News reported full accounts of the viral report and showed images from the video post. The individuals seen in the video were engaged in a political fight and wielding makeshift spears rather than transitioning into a cross-border attack. The Assam Police issued an official response on X (formerly Twitter) that denied the claim, while noting that nothing of that nature occurred in Goalpara nor in any other district of Assam.
Conclusion:
Based on our research, we conclude that the viral video does not show unlawful Bangladeshi immigrants in Assam. It depicts a political clash in Kishoreganj, Bangladesh, on July 1, 2025. The claim attached to the video is completely untrue and is intended to mislead the public as to where and what the incident depicted is.
Claim: Video shows illegal migrants with spears moving in groups to assault police!
Claimed On: Social Media
Fact Check: False and Misleading
Related Blogs

Introduction
Digital Arrests are a form of scam that involves the digital restraint of individuals. These restraints can vary from restricting access to the account(s), and digital platforms, to implementing measures to prevent further digital activities or being restrained on video calling or being monitored through video calling. Typically, these scams target vulnerable individuals who are unfamiliar with digital fraud tactics, making them more susceptible to manipulation. These scams often target the victims on allegations of drug trafficking, money laundering, falsified documents, etc. These are serious crimes and these scammers scare the victim into thinking that either their identities were used to commit these crimes or they have committed these crimes. Recently there has been an uptick in the digital fraud scams in India highlighting the growing concerns.
The Legality of Digital Arrests in India
There is no legal provision for law enforcement to conduct ‘arrests’ via video calls or online monitoring. If you receive such calls, it is a clear scam. In fact, recently enacted new criminal laws do not provide for any provision for law enforcement agencies conducting a digital arrest. The law only provides for service of the summons and the proceedings in an electronic mode.
The Bhartiya Nagrik Suraksha Sanhita (BNSS), 2023 provides for the summons to be served electronically under section 63. The section defines the form of summons. It states that every summons served electronically shall be encrypted and bear the image of the seal of the Court or digital signature. Further, according to section 532 of the BNSS, the trial and proceedings may be held in electronic mode, by use of electronic communication or by the use of audio-video electronic means.
Modus Operandi
Under digital arrest scams, the scammer makes a connection via video calls (WhatsApp calls, skype, etc) with the victim over their alleged involvement in crimes (financial, drug trafficking, etc) in bogus charges. The victims are intimidated that the arrest will take place soon and till the time the arresting officers do not reach the victim they are to remain on the call and be under digital surveillance and not contact anyone during the ongoing investigation.
During this period, the scammers start collecting information from the victim to confirm their identity and create an atmosphere in which multiple senior officials are on the victim’s case and they are investigating the case thoroughly. By this time, the victim, scared out of their wits, sits through this arrest and it is then that the scammers posing as law enforcement officials make comments that they can avoid arrest by paying a certain amount of the fines to the accounts that they specify. This monitoring/ surveillance continues till the time the victim makes the transfers to the accounts provided by the scammers. These are the common manipulation tactics used by scammers in digital arrest fraud.
Recent Cyber Arrest Cases
- Recently a 35-year-old NBCC official was duped of Rs 55 lakh in a 'digital arrest' scam. Posing as customs officials, fraudsters claimed her details were linked to intercepted illegal items and a pending arrest. They kept her on video calls, convincing her to transfer Rs 55 lakh to avoid money laundering charges. After the transfer, the scammers vanished. A police investigation traced the funds to a fake company, leading to the arrest of suspects.
- Another recent case involved a neurologist who was duped Rs 2.81 crores in a ‘digital arrest’ scam. Fraudsters claimed her phone number and Aadhaar was linked to accounts transferring funds to an Individual. Under pressure, she was convinced to undergo “verification” and made multiple transactions over two days. The scammers threatened legal consequences for money laundering if she didn’t comply. Now a police investigation is ongoing, and her immense financial loss highlights the severity of this cybercrime.
- One another case took place where the victim was duped of Rs 7.67 crores in a prolonged ‘digital arrest’ scam over three months. Fraudsters posing as TRAI officials claimed complaints against her phone number and threatened to suspend it, alleging illegal use of another number linked to her Aadhaar. Pressured and manipulated through video calls, the victim was coerced into transferring large sums, even taking an Rs 80 lakh loan. The case is under investigation as authorities pursue the cybercriminals behind the massive fraud.
Best Practices
- Do not panic when you get any calls where sudden unexpected news is shared with you. Scammers thrive on the panic that they create.
- Do not share personal details such as Aadhaar number, PAN number etc with unknown or suspect entities. Be cautious of your personal and financial information such as credit card numbers, OTPs, or any other passwords with anyone.
- If individuals contact, claiming to be government officials, always verify their identities by contacting the entity through the proper channels.
- Report and block any fraudulent communications that are received and mark them as Spam. This would further inform other users if they see the caller ID being marked as fraud or spam.
- If you have been defrauded then report about the same to the authorities so that action can be taken and authorities can arrest the fraudsters.
- Do not transfer any money as part of ‘fines’ or ‘dues’ to the accounts that these calls or messages link to.
- In case of any threat, issue or discrepancy, file a complaint at cybercrime.gov.in or helpline number 1930. You can also seek assistance from the CyberPeace helpline at +91 9570000066.
References:
- https://www.cyberpeace.org/resources/blogs/digital-arrest-fraud
- https://www.business-standard.com/india-news/what-is-digital-house-arrest-find-out-how-to-avoid-this-new-scam-124052400799_1.html
- https://www.the420.in/ias-ips-officers-major-generals-doctors-and-professors-fall-victim-to-digital-arrest-losing-crores-stay-alert-read-5-real-cases-inside/
- https://indianexpress.com/article/cities/delhi/senior-nbcc-official-duped-in-case-of-digital-arrest-3-arrested-delhi-police-9588418/#:~:text=Of%20the%20duped%20amount%2C%20Rs,a%20Delhi%20police%20officer%20said (case study 1)
- https://timesofindia.indiatimes.com/city/lucknow/lucknow-sgpgims-professor-duped-of-rs-2-81-crore-in-digital-arrest-scam/articleshow/112521530.cms (case study 2)
- https://timesofindia.indiatimes.com/city/jaipur/bits-prof-duped-of-7-67cr-cops-want-cbi-probe-in-case/articleshow/109514200.cms (case study 3)
.webp)
In the tapestry of our modern digital ecosystem, a silent, pervasive conflict simmers beneath the surface, where the quest for cyber resilience seems Sisyphean at times. It is in this interconnected cyber dance that the obscure orchestrator, StripedFly, emerges as the maestro of stealth and disruption, spinning a complex, mostly unseen web of digital discord. StripedFly is not some abstract concept; it represents a continual battle against the invisible forces that threaten the sanctity of our digital domain.
This saga of StripedFly is not a tale of mere coincidence or fleeting concern. It is emblematic of a fundamental struggle that defines the era of interconnected technology—a struggle that is both unyielding and unforgiving in its scope. Over the past half-decade, StripedFly has slithered its way into over a million devices, creating a clandestine symphony of cybersecurity breaches, data theft, and unintentional complicity in its agenda. Let's delve deep into this grand odyssey to unravel the odious intricacies of StripedFly and assess the reverberations felt across our collective pursuit of cyber harmony.
The StripedFly malware represents the epitome of a digital chameleon, a master of cyber camouflage, masquerading as a mundane cryptocurrency miner while quietly plotting the grand symphony of digital bedlam. Its deceptive sophistication has effortlessly skirted around the conventional tripwires laid by our cybersecurity guardians for years. The Russian cybersecurity giant Kaspersky's encounter with StripedFly in 2017 brought this ghostly figure into the spotlight—hitherto, a phantom whistling past the digital graveyard of past threats.
How Does it work
Distinctive in its composition, StripedFly conceals within its modular framework the potential for vast infiltration—an exploitation toolkit designed to puncture the fortifications of both Linux and Windows systems. In an emboldened maneuver, it utilizes a customized version of the EternalBlue SMBv1 exploit—a technique notoriously linked to the enigmatic Equation Group. Through such nefarious channels, StripedFly not only deploys its malicious code but also tenaciously downloads binary files and executes PowerShell scripts with a sinister adeptness unbeknownst to its victims.
Despite its insidious nature, perhaps its most diabolical trait lies in its array of plugin-like functions. It's capable of exfiltrating sensitive information, erasing its tracks, and uninstalling itself with almost supernatural alacrity, leaving behind a vacuous space where once tangible evidence of its existence resided.
In the intricate chess game of cyber threats, StripedFly plays the long game, prioritizing persistence over temporary havoc. Its tactics are calculated—the meticulous disabling of SMBv1 on compromised hosts, the insidious utilization of pilfered keys to propagate itself across networks via SMB and SSH protocols, and the creation of task scheduler entries on Windows systems or employing various methods to assert its nefarious influence within Linux environments.
The Enigma around the Malware
This dualistic entity couples its espionage with monetary gain, downloading a Monero cryptocurrency miner and utilizing the shadowy veils of DNS over HTTPS (DoH) to camouflage its command and control pool servers. This intricate masquerade serves as a cunning, albeit elaborate, smokescreen, lulling security mechanisms into complacency and blind spots.
StripedFly goes above and beyond in its quest to minimize its digital footprint. Not only does it store its components as encrypted data on code repository platforms, deftly dispersed among the likes of Bitbucket, GitHub, and GitLab, but it also harbors a bespoke, efficient TOR client to communicate with its cloistered C2 server out of sight and reach in the labyrinthine depths of the TOR network.
One might speculate on the genesis of this advanced persistent threat—its nuanced approach to invasion, its parallels to EternalBlue, and the artistic flare that permeates its coding style suggest a sophisticated architect. Indeed, the suggestion of an APT actor at the helm of StripedFly invites a cascade of questions concerning the ultimate objectives of such a refined, enduring campaign.
How to deal with it
To those who stand guard in our ever-shifting cyber landscape, the narrative of StripedFly is a clarion call. StObjective reminders of the trench warfare we engage in to preserve the oasis of digital peace within a desert of relentless threats. The StripedFly chronicle stands as a persistent, looming testament to the necessity for heeding the sirens of vigilance and precaution in cyber practice.
Reaffirmation is essential in our quest to demystify the shadows cast by StripedFly, as it punctuates the critical mission to nurture a more impregnable digital habitat. Awareness and dedication propel us forward—the acquisition of knowledge regarding emerging threats, the diligent updating and patching of our systems, and the fortification of robust, multilayered defenses are keystones in our architecture of cyber defense. Together, in concert and collaboration, we stand a better chance of shielding our digital frontier from the dim recesses where threats like StripedFly lurk, patiently awaiting their moment to strike.
References:
https://thehackernews.com/2023/11/stripedfly-malware-operated-unnoticed.html?m=1

Today, let us talk about one of the key features of our digital lives – security. The safer their online habits are, the safer their data and devices will be. A branded security will make their devices and Internet connections secure, but their carelessness or ignorance can make them targets for cybercrimes. On the other hand, they can themselves unwittingly get involved in dubious activities online. With children being very smart about passwords and browsing history clearing, parents are often left in the dark about their digital lives.
Fret not, parental controls are there at your service. These are digital tools often included with your OS or security software package, which helps you to remotely monitor and control your child’s online activities.
Where Can I find them?
Many devices come with pre-installed PC tools that you have to set up and run. Go to Settings-> Parental controls or Screentime and proceed from there. As I mentioned, they are also offered as a part of your comprehensive security software package.
Why and How to Use Parental Controls
Parental controls help monitor and limit your children's smartphone usage, ensuring they access only age-appropriate content. If your child is a minor, use of this tool is recommended, with the full knowledge of your child/ren. Let them know that just as you supervise them in public places for their safety, and guide them on rights and wrongs, you will use the tool to monitor and mentor them online, for their safety. Emphasize that you love them and trust them but are concerned about the various dubious and fake characters online as well as unsafe websites and only intend to supervise them. As they grow older and display greater responsibility and maturity levels, you may slowly reduce the levels of monitoring. This will help build a relationship of mutual trust and respect.
Step 1: Enable Parental Controls
- iOS: If your child has an iPhone, to set up the controls, go to Settings, select Screen Time, then select Content & Privacy Restrictions.
- Android: If the child has an Android phone, you can use the Google Family Link to manage apps, set screen time limits, and track device usage.
- Third-party apps: Consider security tools like McAfee, Kaspersky, Bark, Qustodio, or Norton Family for advanced features.
Check out what some of the security software apps have on offer:





If you prefer Norton, here are the details:
McAfee Parental Controls suite offers the following features:

McAfee also outlines why Parental Controls matter:

Lastly, let us take a look at what Quick Heal has on offer:

STEP 2: Set up Admin Login
Needless to say, a parent should be the admin login, and it is a wise idea to set up a strong and unique password. You do not want your kids to outsmart you and change their accessibility settings, do you? Remember to create a password you will remember, for children are clever and will soon discover where you have jotted it down.
STEP 3: Create Individual accounts for all users of the device
Let us say two minor kids, a grandparent and you, will be using the device. You will have to create separate accounts for each user. You can allow the children to choose their own passwords, it will give them a sense of privacy. The children or you may (or may not) need to help any Seniors set up their accounts.
Done? Good. Now let us proceed to the next step.
STEP 4: Set up access permissions by age
Let us first get grandparents and other seniors out of the way by giving them full access. when you enter their ages; your device will identify them as adults and guide you accordingly.
Now for each child, follow the instructions to set up filters and blocks. This will again vary with age – more filters for the younger ones, while you can remove controls gradually as they grow older, and hence more mature and responsible. Set up screen Time (daily and weekends), game filtering and playtime, content filtering and blocking by words (e.g. block websites that contain violence/sex/abuse). Ask for activity reports on your device so that you can monitor them remotely This will help you to receive alerts if children connect with strangers or get involved in abusive actions.
Save the data and it has done! Simple, wasn’t it?
Additional Security
For further security, you may want to set up parental controls on the Home Wi-Fi Router, Gaming devices, and online streaming services you subscribe to.
Follow the same steps. Select settings, Admin sign-in, and find out what controls or screen time protection they offer. Choose the ones you wish to activate, especially for the time when adults are not at home.
Conclusion
Congratulations. You have successfully secured your child’s digital space and sanitized it. Discuss unsafe practices as a family, and make any digital rule breaches and irresponsible actions, or concerns, learning points for them. Let their takeaway be that parents will monitor and mentor them, but they too have to take ownership of their actions.


