Unveiling Digital Insights: Navigating the World of Digital Forensics
Introduction:
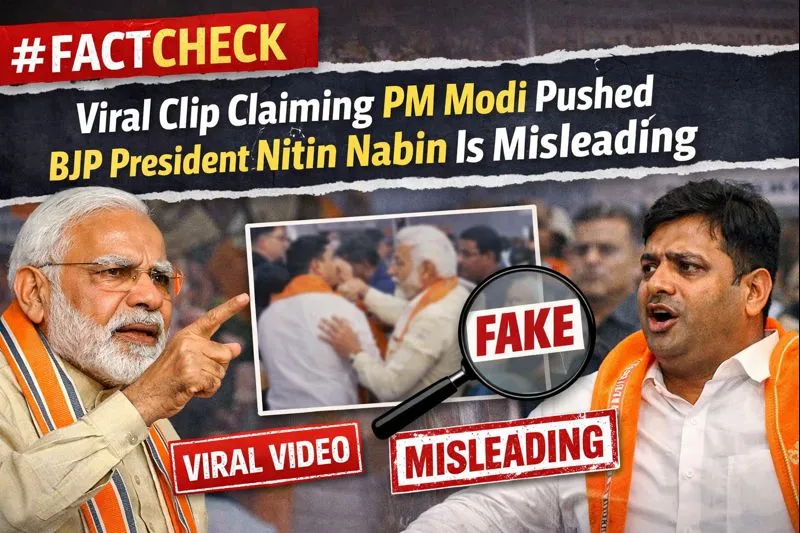
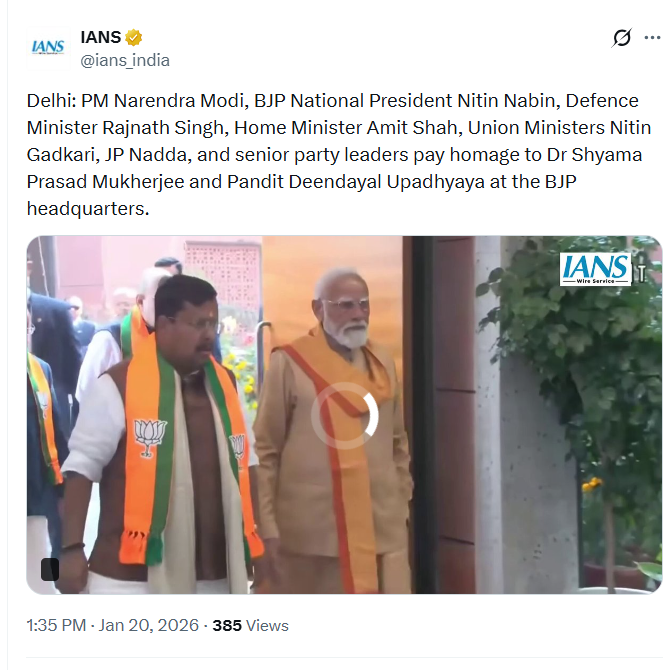
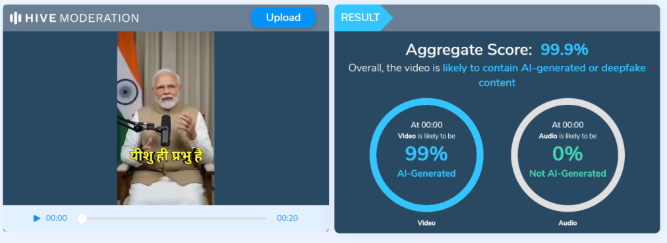
Digital Forensics, as the term goes, “It is the process of collecting, preserving, identifying, analyzing, and presenting digital evidence in a way that the evidence is legally admitted.”
It is like a detective work in the digital realm, where investigators use various specific methods to find deleted files and to reveal destroyed messages.
The reason why Digital Forensics is an important field is because with the advancement of technology and the use of digital devices, the role of Digital Forensics in preserving the evidence and protecting our data from cybercrime is becoming more and more crucial.
Digital Forensics is used in various situations such as:
- Criminal Investigations: Digital Forensics enables investigators to trace back cyber threat actors and further identify victims of the crime to gather evidence needed to punish criminals.
- Legal issues: Digital Forensics might aid in legal matters involving intellectual property infringement and data breaches etc.
Types of Digital Data in Digital Forensics:
1.Persistent (Non-volatile) Data :-
- This type of Data Remains Intact When The Computer Is Turned Off.
- ex. Hard-disk, Flash-drives
2. Volatile Data :-
- These types of Data Would Be Lost When The Computer Is Turned Off.
- ex. Temp. Files, Unsaved OpenFiles, etc.
The Digital Forensics Process
The process is as follows

- Evidence Acquisition: This process involves making an exact copy (forensic image) of the storage devices such as hard drives, SSD or mobile devices. The goal is to preserve the original data without changing it.
- Data Recovery: After acquiring the forensic image, the analysts use tools to recover deleted, hidden or the encrypted data inside the device .
- Timeline Analysis: Analysts use timestamp information from files, and system logs to reconstruct the timeline of activities on a device. This helps in understanding how an incident spanned out and who was involved in it.
- Malware Analysis: In cases involving security breaches, analysts analyze malware samples to understand their behavior, impact, and origins. various reverse engineering techniques are used to analyze the malicious code.
Types of tools:
- Faraday Bags: Faraday bags are generally the first step in digital evidence capture. These bags are generally made of conductive materials, which are used to shield our electronic devices from external waves such as WiFi, Bluetooth, and mobile cellular signals, which in turn protects the digital evidence from external tampering.
- Data recovery : These types of software are generally used for the recovery of deleted files and their associated data. Ex. Magnet Forensics, Access data, X-Ways
- Disk imaging and analysis :These types of softwares are Generally used to replicate the data storage devices and then perform further analysis on it ex. FTKImager, Autopsy, and, Sleuth Kit
- File carving tools: They are generally used to extract information from the embedded files in the image made. Ex.Foremost, Binwalk, Scalpel
Some common tools:
- EnCase: It is a tool for acquiring, analyzing, and reporting digital evidence.
- Autopsy: It is an open-source platform generally used for analyzing hard drives and smartphones.
- Volatility: It is a framework used generally for memory forensics to analyze volatile memory dumps and extract info.
- Sleuth Kit: It is a package of CLI tools for investigating disk images and its associated file systems.
- Cellebrite UFED: It is a tool generally used for mobile forensics.
Challenges in the Field:
- Encryption: Encryption plays a major challenge as the encrypted data requires specialized techniques and tools for decryption.
- Anti-Forensic Techniques: Anti-Forensics techniques play a major challenge as the criminals often use anti-forensic methods to cover their tracks, making it challenging to get the digital evidence.
- Data Volume and Complexity: The large volume of digital data and the diversity of various devices create challenges in evidence collection and analysis.
The Future of Digital Forensics: A Perspective
With the growth of technology and the vast presence of digital data, the challenges and opportunities in Digital Forensics keep on updating themselves. Due to the onset of new technology and the ever growing necessity of cloud storage, mobile devices, and the IoT (Internet of Things), investigators will have to develop new strategies and should be ready to adapt and learn from the new shaping of the tech world.
Conclusion:
Digital Forensics is an essential field in the recent era for ensuring fairness in the digital era. By collecting, inspecting, and analyzing the digital data, the Digital Forensics investigators can arrive lawfully at the prosecution of criminals and the settlement of civil disputes. Nowadays with technology on one hand progressing continuously, the discipline of Digital Forensics will certainly become even more pivotal in the case of investigations in the years to come.