#FactCheck! Viral Image Claiming Virat Kohli and Rohit Sharma Visited Kedarnath Is AI-Generated
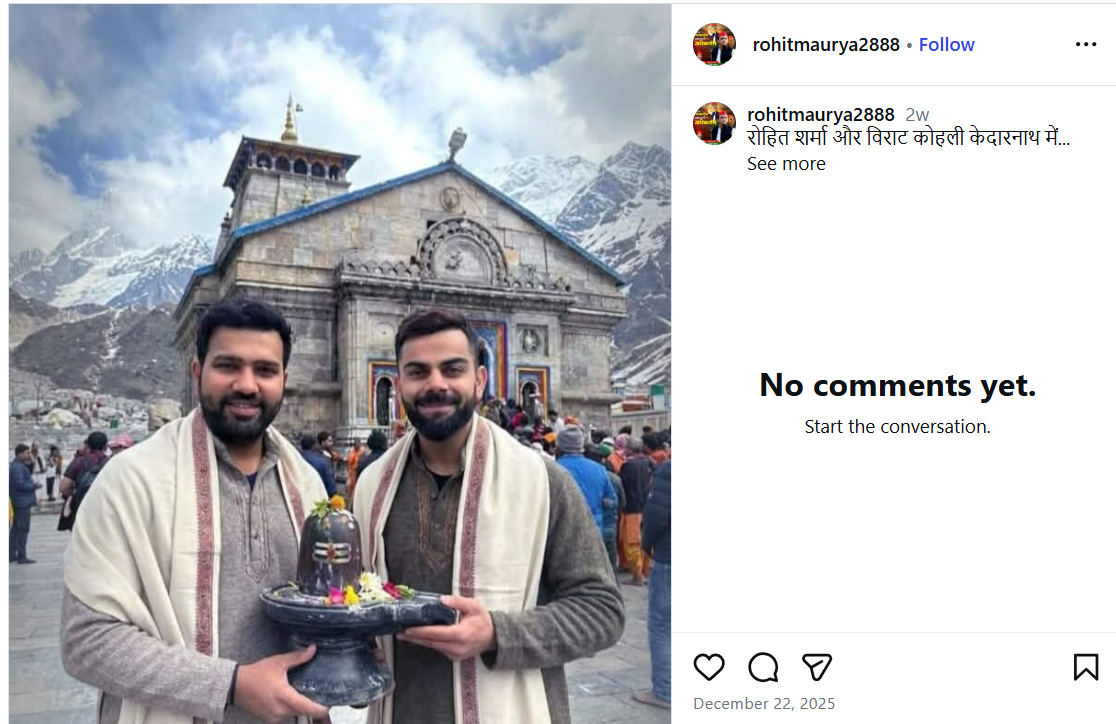
A photo featuring Indian cricketers Virat Kohli and Rohit Sharma is being widely shared on social media. In the image, both players are seen holding a Shivling, with the Kedarnath temple visible in the background. Users sharing the image claim that Virat Kohli and Rohit Sharma recently visited Kedarnath.
However, CyberPeace Foundation’s investigation found the claim to be false. Our verification established that the viral image is not real but has been created using Artificial Intelligence (AI) and is being circulated with a misleading narrative.
The Claim
An Instagram user shared the viral image on December 22, 2025, with the caption stating that Rohit Sharma and Virat Kohli are in Kedarnath. The post has since been widely reshared by other users, who assumed the image to be authentic. Link, archive link, screenshot:
Fact Check
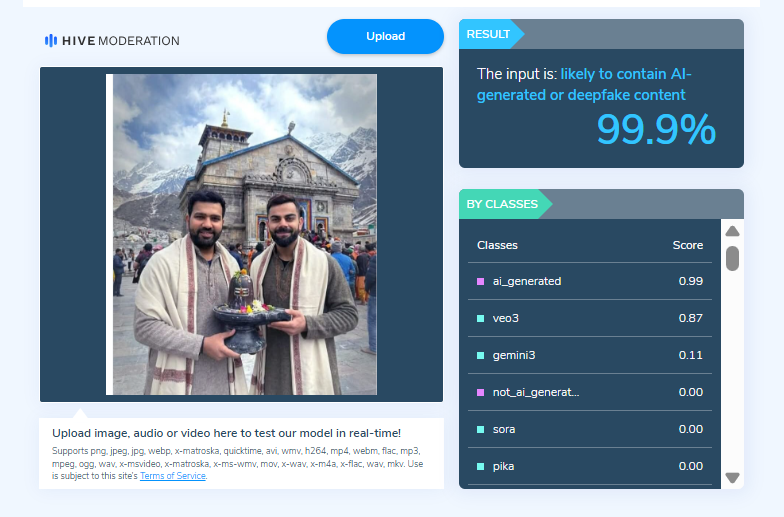
On closely examining the viral image, the Desk noticed visual inconsistencies suggesting that it may be AI-generated. To verify this, the image was scanned using the AI detection tool HIVE Moderation. According to the results, the image was found to be 99 per cent AI-generated.
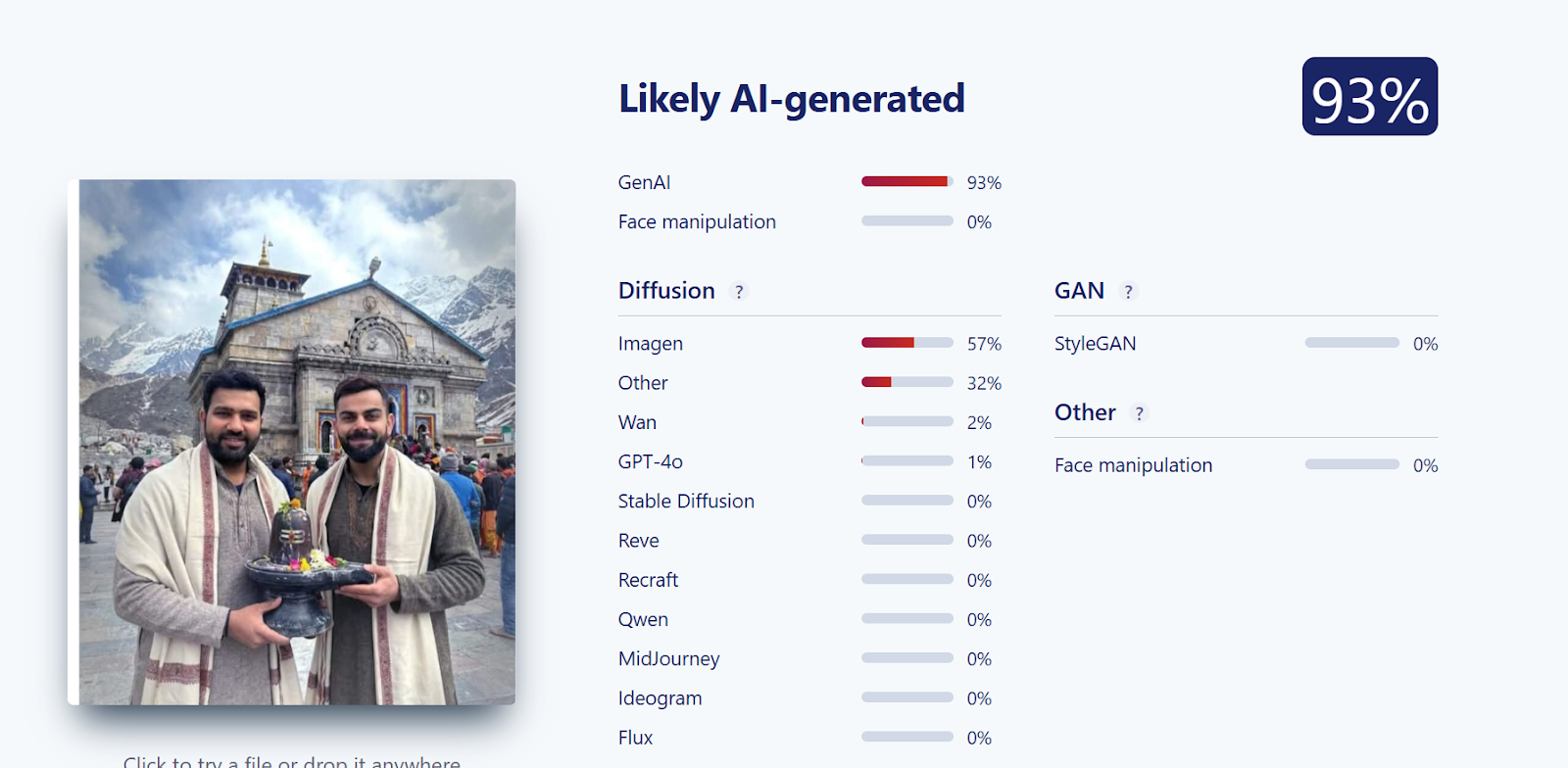
Further verification was conducted using another AI detection tool, Sightengine. The analysis revealed that the image was 93 per cent likely to be AI-generated, reinforcing the findings from the previous tool.
Conclusion
CyberPeace Foundation’s research confirms that the viral image claiming Virat Kohli and Rohit Sharma visited Kedarnath is fabricated. The image has been generated using AI technology and is being falsely shared on social media as a real photograph.
Related Blogs

Executive Summary:
A video circulating on Social media has claimed that Iran has launched a missile strike destroying Ben Gurion Airport in Tel Aviv. With rising tensions in geopolitics, the video quickly became popular. However, our research has detailed inspections through digital verification tools and visual analysis showed that the video is AI-generated. No incident or damage ever occurred.

Claim:
A viral video circulating on social media platforms claims to show Tel Aviv’s Ben Gurion Airport destroyed following an Iranian missile strike. The video is being shared with captions suggesting it is the last recorded visuals from the attack, with some users asserting it as evidence of escalating conflict between Iran and Israel.

Fact Check:
After looking into the video that purported to show the destruction of Tel Aviv's Ben Gurion Airport in an Iranian missile strike, we researched the topic whether the claim is accurate or not. The video depicts a damaged airport terminal, with debris and fires, but a visual analysis determined that there were a number of suspicious characteristics: asymmetrical layout, artificial-looking smoke patterns, and the absence of activity or humans—those are all typical indications of AI generation. Our research traced the origins of the video to an Instagram post, with a date of May 27, 2025, made by what seems to be a user who frequently shares AI-generated images.


In order to verify our conclusions, we used Hive Moderation, an AI content detection tool, which produced a result of an 80% probability that the video is altered, and this level of probability strongly supports the idea that the footage is not real. Additionally, reports from popular organizations like India Today and Reuters supported these results. All findings resulting from our research established that the video is synthetic and unrelated to any event occurring at Ben Gurion Airport, and therefore debunked a false narrative propagated on social media.

To confirm, we also compared the visuals with a real aerial image of Tel Aviv’s Ben Gurion Airport available on aviation stock sites.



Fig: Google Maps image of Tel Aviv’s Ben Gurion Airport
The visuals from the viral video are not real locations or scenes of Aviv’s Ben Gurion Airport's true location and configuration therefore it is fake and misleading.
Conclusion:
After thorough research it is concluded that the viral video is fake and it is not an actual missile strike at Ben Gurion Airport. The video is made with AI, and posted by a content creator of synthetic content well before any conflict update. There is no official confirmation or credible news coverage to substantiate the claim, with a high probability of AI-detection, and it has been proven to be digitally manipulated. Therefore, the claim is untrue and misleading.
- Claim: A video shows Iran's missile strike destroying Tel Aviv’s Ben Gurion Airport.
- Claimed On: Social Media
- Fact Check: False and Misleading

Introduction
The advancement of technology has brought about remarkable changes in the aviation industry, including the introduction of inflight internet access systems. While these systems provide passengers with connectivity during their flights, they also introduce potential vulnerabilities that can compromise the security of aircraft systems.
Inflight Internet Access Systems
Inflight internet access systems have become integral to the modern air travel experience, allowing passengers to stay connected even at 30,000 feet. However, these systems can also be attractive targets for hackers, raising concerns about the safety and security of aircraft operations.
The Vulnerabilities of Inflight Internet Access Systems:
Securing Networked Avionics
Avionics, the electronic systems that support aircraft operation, play a crucial role in flight safety and navigation. While networked avionics are designed with robust security measures, they are not invulnerable to cyber threats. Therefore, it is essential to implement comprehensive security measures to protect these critical systems.
- Ensuring Robust Architecture: Networked avionics should be designed with a strong focus on security. Implementing secure network architectures, such as segmentation and isolation, can minimise the risk of unauthorised access and limit the potential impact of a breach.
- Rigorous Security Testing: Avionics systems should undergo rigorous security testing to identify vulnerabilities and weaknesses. Regular assessments, penetration testing, and vulnerability scanning are essential to proactively address any security flaws.
- Collaborative Industry Efforts: Collaboration between manufacturers, airlines, regulatory bodies, and security researchers is crucial in strengthening the security of networked avionics. Sharing information, best practices, and lessons learned can help identify and address emerging threats effectively.
- Continuous Monitoring and Updtes: Networked avionics should be continuously monitored for any potential security breaches. Prompt updates and patches should be applied to address newly discovered vulnerabilities and protect against known attack vectors.
Best practices to be adopted for the security of Aircraft Systems
- Holistic Security Approach: Recognizing the interconnectedness of inflight internet access systems and networked avionics is essential. A holistic security approach should be adopted to address vulnerabilities in both systems and protect the overall aircraft infrastructure.
- Comprehensive Security Measures: The security of inflight internet access systems should be on par with any other internet-connected device. Strong authentication, encryption, intrusion detection, and prevention systems should be implemented to mitigate risks and ensure the integrity of data transmissions.
- Responsible Practices and Industry Collaboration: Encouraging responsible practices and fostering collaboration between security researchers and industry stakeholders can accelerate the identification and remediation of vulnerabilities. Open communication channels and a cooperative mindset are vital in addressing emerging threats effectively.
- Robust Access Controls: Strong access controls, such as multi-factor authentication and role-based access, should be implemented to limit unauthorised access to avionics systems. Only authorised personnel should have the necessary privileges to interact with these critical systems.
Conclusion
Inflight internet access systems bring convenience and connectivity to air travel but also introduce potential risks to the security of aircraft systems. It is crucial to understand and address the vulnerabilities associated with these systems to protect networked avionics and ensure passenger safety. By implementing robust security measures, conducting regular assessments, fostering collaboration, and adopting a comprehensive approach to aircraft cybersecurity, the aviation industry can mitigate the risks and navigate the sky with enhanced safety and confidence. Inflight internet access systems and networked avionics are vital components of modern aircraft, providing connectivity and supporting critical flight operations. Balancing connectivity and cybersecurity is crucial to ensure the safety and integrity of aircraft systems.
.jpeg)
Introduction and Brief Analysis
A movie named “The Artifice Girl” portrayed A law enforcement agency developing an AI-based personification of a 12-year-old girl who appears to be exactly like a real person. Believing her to be an actual girl, perpetrators of child sexual exploitation were caught attempting to seek sexual favours. The movie showed how AI aided law enforcement, but the reality is that the emergence of Artificial Intelligence has posed numerous challenges in multiple directions. This example illustrates both the promise and the complexity of using AI in sensitive areas like law enforcement, where technological innovation must be carefully balanced with ethical and legal considerations.
Detection and Protection tools are constantly competing with technologies that generate content, automate grooming and challenge legal boundaries. Such technological advancements have provided enough ground for the proliferation of Child Sexual Exploitation and Abuse Material (CSEAM). Also known as child pornography under Section 2 (da) of Protection of Children from Sexual Offences Act, 2012, it defined it as - “means any visual depiction of sexually explicit conduct involving a child which includes a photograph, video, digital or computer-generated image indistinguishable from an actual child and image created, adapted, or modified, but appears to depict a child.”
Artificial Intelligence is a category of technologies that attempt to shape human thoughts and behaviours using input algorithms and datasets. Two Primary applications can be considered in the context of CSEAM: classifiers and content generators. Classifiers are programs that learn from large data sets, which may be labelled or unlabelled and further classify what is restricted or illegal. Whereas generative AI is also trained on large datasets, it uses that knowledge to create new things. Majority of current AI research related to AI for CSEAM is done by the use of Artificial neural networks (ANNs), a type of AI that can be trained to identify unusual connections between items (classification) and to generate unique combinations of items (e.g., elements of a picture) based on the training data used.
Current Legal Landscape
The legal Landscape in terms of AI is yet unclear and evolving, with different nations trying to track the evolution of AI and develop laws. However, some laws directly address CSEAM. The International Centre for Missing and Exploited Children (ICMEC) combats Illegal sexual content involving children. They have a “Model Legislation” for setting recommended sanctions/sentencing. According to research performed in 2018, Illegal sexual content involving children is illegal in 118 of the 196 Interpol member states. This figure represents countries that have sufficient legislation in place to meet 4 or 5 of the 5 criteria defined by the ICMEC.
CSEAM in India can be reported on various portals like the ‘National Cyber Crime Reporting Portal’. Online crimes related to children, including CSEAM, can be reported to this portal by visiting cybercrime.gov.in. This portal allows anonymous reporting, automatic FIR registration and tracking of your complaint. ‘I4C Sahyog Portal’ is another platform managed by the Indian Cyber Crime Coordination Centre (I4C). This portal integrates with social media platforms.
The Indian legal front for AI is evolving and CSEAM is well addressed in Indian laws and through judicial pronouncements. The Supreme Court judgement on Alliance and Anr v S Harish and ors is a landmark in this regard. The following principles were highlighted in this judgment.
- The term “child pornography” should be substituted by “Child Sexual Exploitation and Abuse Material” (CSEAM) and shall not be used for any further judicial proceeding, order, or judgment. Also, parliament should amend the same in POCSO and instead, the term CSEAM should be endorsed.
- Parliament to consider amending Section 15 (1) of POCSO to make it more convenient for the general public to report by way of an online portal.
- Implementing sex education programs to give young people a clear understanding of consent and the consequences of exploitation. To help prevent Problematic sexual behaviour (PSB), schools should teach students about consent, healthy relationships and appropriate behaviour.
- Support services to the victims and rehabilitation programs for the offenders are essential.
- Early identification of at-risk individuals and implementation of intervention strategies for youth.
Distinctive Challenges
According to a report by the National Centre for Missing and Exploited Children (NCMEC), a significant number of reports about child sexual exploitation and abuse material (CSEAM) are linked to perpetrators based outside the country. This highlights major challenges related to jurisdiction and anonymity in addressing such crimes. Since the issue concerns children and considering the cross-border nature of the internet and the emergence of AI, Nations across the globe need to come together to solve this matter. Delays in the extradition procedure and irregular legal processes across the jurisdictions hinder the apprehension of offenders and the delivery of justice to victims.
CyberPeace Recommendations
For effective regulation of AI-generated CSEAM, laws are required to be strengthened for AI developers and trainers to prevent misuse of their tools. AI should be designed with its ethical considerations, ensuring respect for privacy, consent and child rights. There can be a self-regulation mechanism for AI models to recognise and restrict red flags related to CSEAM and indicate grooming or potential abuse.
A distinct Indian CSEAM reporting portal is urgently needed, as cybercrimes are increasing throughout the nation. Depending on the integrated portal may lead to ignorance of AI-based CSEAM cases. This would result in faster response and focused tracking. Since AI-generated content is detectable. The portal should also include an automated AI-content detection system linked directly to law enforcement for swift action.
Furthermore, International cooperation is of utmost importance to win the battle of AI-enabled challenges and to fill the jurisdictional gaps. A united global effort is required. Using a common technology and unified international laws is essential to tackle AI-driven child sexual exploitation across borders and protect children everywhere. CSEAM is an extremely serious issue. Children are among the most vulnerable to such harmful content. This threat must be addressed without delay, through stronger policies, dedicated reporting mechanisms and swift action to protect children from exploitation.
References:
- https://www.sciencedirect.com/science/article/pii/S2950193824000433?ref=pdf_download&fr=RR-2&rr=94efffff09e95975
- https://aasc.assam.gov.in/sites/default/files/swf_utility_folder/departments/aasc_webcomindia_org_oi d_4/portlet/level_2/pocso_act.pdf
- https://www.manupatracademy.com/assets/pdf/legalpost/just-rights-for-children-alliance-and-anr-vs-sharish-and-ors.pdfhttps://www.icmec.orghttps://www.missingkids.org/theissues/generative-ai


