#FactCheck - Edited Video Falsely Attributed to Arnab Goswami; Claim of Remarks Against Prime Minister Modi Is Misleading
A video has been going viral on social media in recent days in which Republic TV’s Editor-in-Chief and anchor Arnab Goswami can allegedly be heard using objectionable language against Prime Minister Narendra Modi. While sharing the video, users are claiming that Arnab Goswami publicly made controversial remarks about the Prime Minister.
An investigation by CyberPeace Foundation found this claim to be completely false. Our probe revealed that the viral video is edited and is being circulated on social media with a misleading narrative. In the original video, Arnab Goswami was not making any personal statement; rather, he was referring to an old statement made by Congress leader Rahul Gandhi.
Viral Claim
An Instagram user posted this video on 5 January 2026. In the video, a voice resembling Arnab Goswami is heard saying, “Ye jo Narendra Modi hain, ye chhe mahine baad ghar se nahi nikal paayenge aur Hindustan ke log inhein danda maarenge.”
(Translation: “This Narendra Modi will not be able to step out of his house after six months, and the people of India will beat him with sticks.”)
The post link, its archive link, and screenshots can be seen below:
- Instagram link: https://www.instagram.com/reel/DTHrO7bk7Rf/?igsh=MThzbzBlcm82eWN0ZA%3D%3D
- Archive link: https://archive.ph/oaYsf
Fact Check
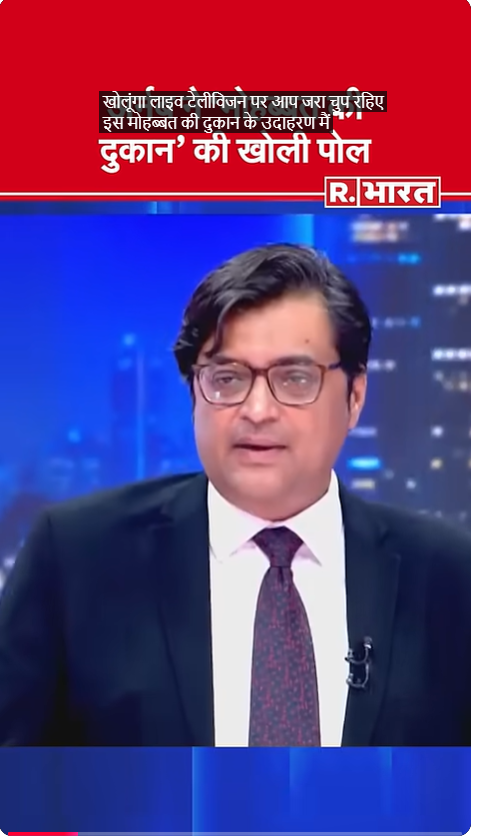
To verify the viral claim, we first examined the video using Google Lens search. During this process, we found a video published on 18 July 2024 on the official YouTube channel of Republic Bharat. The investigation revealed that this video is the longer (extended) version of the viral clip.
After carefully watching the full video, it became clear that Arnab Goswami was not making the statement himself. Instead, he was referring to a remark made by Congress leader Rahul Gandhi during the 2020 Delhi Assembly elections against Prime Minister Narendra Modi. This confirms that the viral video was clipped and presented out of context.
The related video link can be seen below: https://www.youtube.com/shorts/KlQV25-3l8s
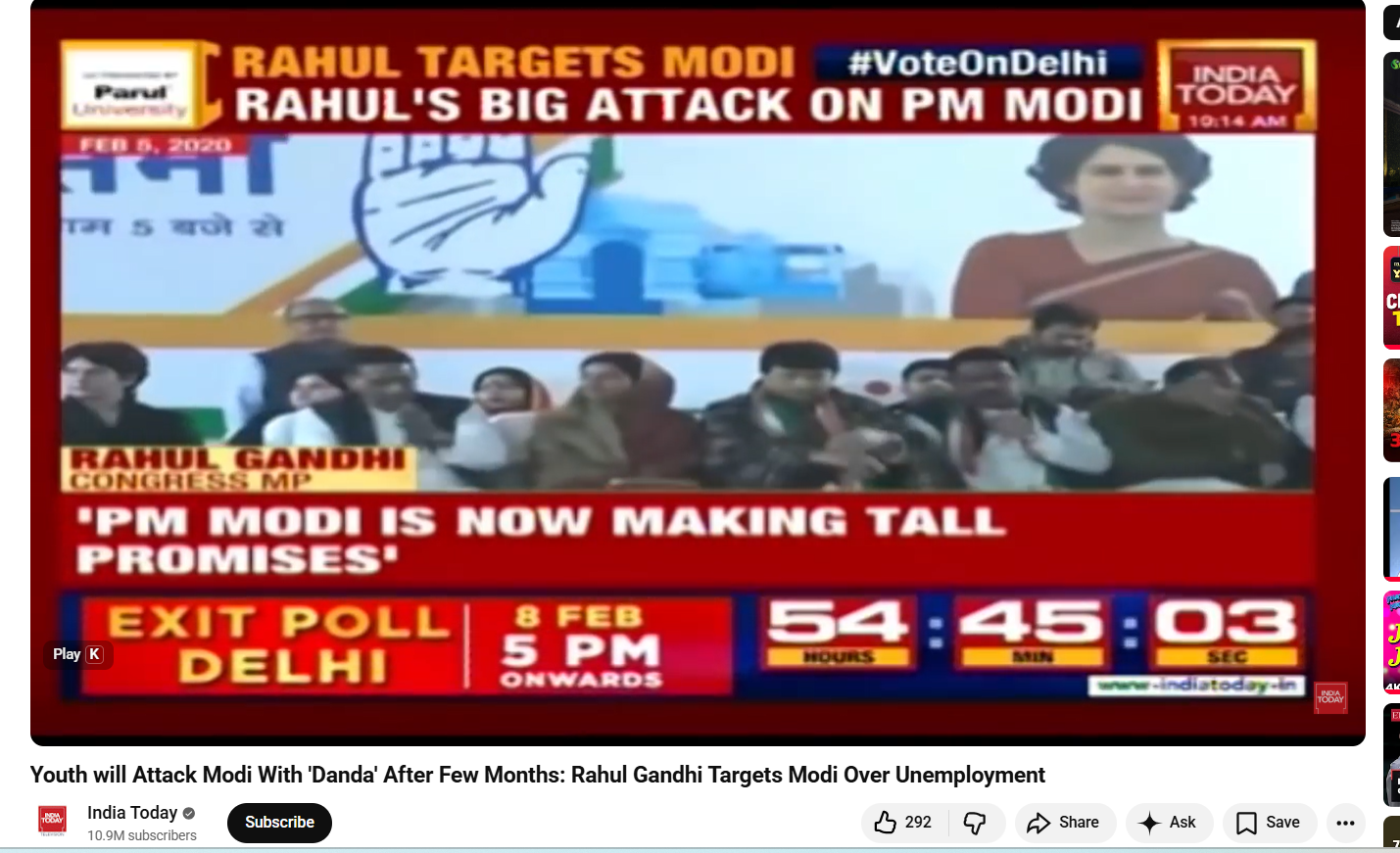
In the next step of the investigation, to verify whether Rahul Gandhi had indeed made such a statement, we conducted a customized keyword search on Google. During this, we found a video published on 6 February 2020 on the official YouTube channel of India Today.
In this video, recorded during a public event ahead of the 2020 Delhi Assembly elections, Rahul Gandhi is seen sharply attacking Prime Minister Narendra Modi, stating that if the Prime Minister fails to resolve the issue of unemployment in the country, the youth would beat him with sticks.
The video link is given below: https://www.youtube.com/watch?v=t5qCSA5nG9Y
Conclusion
The CyberPeace Foundation’s investigation found this claim to be completely fake. The viral video is edited and is being shared in a misleading context. In the original video, Arnab Goswami was referring to an old statement made by Rahul Gandhi, which was selectively clipped and presented in a way that falsely suggests Arnab Goswami himself made objectionable remarks against Prime Minister Narendra Modi.
Related Blogs

Introduction
As e-sports flourish in India, mobile gaming platforms and apps have contributed massively to this boom. The wave of online mobile gaming has led to a new recognition of esports. As we see the Sports Ministry being very proactive for e-sports and e-athletes, it is pertinent to ensure that we do not compromise our cyber security for the sake of these games. When we talk about online mobile gaming, the most common names that come to our minds are PUBG and BGMI. As news for all Indian gamers, BGMI is set to be relaunched in India after approval from the Ministry of Electronics and Information Technology.
Why was BGMI banned?
The Govt banned Battle Ground Mobile India on the pretext of being a Chinese application and the fact that all the data was hosted in China itself. This caused a cascade of compliance and user safety issues as the Data was stored outside India. Since 2020 The Indian Govt has been proactive in banning Chinese applications, which might have an adverse effect on national security and Indian citizens. Nearly 200 plus applications have been banned by the Govt, and most of them were banned due to their data hubs being in China. The issue of cross-border data flow has been a key issue in Geo-Politics, and whoever hosts the data virtually owns it as well and under the potential threat of this fact, all apps hosting their data in China were banned.
Why is BGMI coming back?
BGMI was banned for not hosting data in India, and since the ban, the Krafton Inc.-owned game has been engaging in Idnai to set up data banks and servers to have a separate gaming server for Indian players. These moves will lead to a safe gaming ecosystem and result in better adherence to the laws and policies of the land. The developers have not declared a relaunch date yet, but the game is expected to be available for download for iOS and Android users in the coming few days. The game will be back on app stores as a letter from the Ministry of Electronics and Information Technology has been issued stating that the games be allowed and made available for download on the respective app stores.
Grounds for BGMI
BGMI has to ensure that they comply with all the laws, policies and guidelines in India and have to show the same to the Ministry to get an extension on approval. The game has been permitted for only 90 days (3 Months). Hon’ble MoS Meity Rajeev Chandrashekhar stated in a tweet “This is a 3-month trial approval of #BGMI after it has complied with issues of server locations and data security etc. We will keep a close watch on other issues of User harm, Addiction etc., in the next 3 months before a final decision is taken”. This clearly shows the magnitude of the bans on Chinese apps. The ministry and the Govt will not play the soft game now, it’s all about compliance and safeguarding the user’s data.
Way Forward
This move will play a significant role in the future, not only for gaming companies but also for other online industries, to ensure compliance. This move will act as a precedent for the issue of cross-border data flow and the advantages of data localisation. It will go a long way in advocacy for the betterment of the Indian cyber ecosystem. Meity alone cannot safeguard the space completely, it is a shared responsibility of the Govt, industry and netizens.
Conclusion
The advent of online mobile gaming has taken the nation by storm, and thus, being safe and secure in this ecosystem is paramount. The provisional permission form BGMI shows the stance of the Govt and how it is following the no-tolerance policy for noncompliance with laws. The latest policies and bills, like the Digital India Act, Digital Personal Data Protection Act, etc., will go a long way in securing the interests and rights of the Indian netizen and will create a blanket of safety and prevention of issues and threats in the future.

Introduction
Purchasing online currencies through one of the numerous sizable digital marketplaces designed specifically for this purpose is the simplest method. The quantity of cryptocurrency and money paid. These online marketplaces impose an exchange fee. After being obtained, digital cash is stored in a digital wallet and can be used in the metaverse or as real money to make purchases of goods and services in the real world. Blockchain ensures the security and decentralisation of each exchange.
Its worth and application are comparable to those of gold: when a large number of investors choose this valuable asset, its value increases and vice versa. This also applies to cryptocurrencies, which explains why they have become so popular in recent years. The metaphysical realm is an online space where users can communicate with one another via virtual personas, among other features. Furthermore, money and commerce always come up when people communicate.
Web3 is welcoming the metaverse, and in an environment where conventional currency isn't functional, its technologies are making it possible to use cryptocurrencies. Non-Fungible Tokens (NFTs) can be used to monitor intellectual rights to ownership in the metaverse, while cryptocurrencies are used to pay for content and incentivise consumers. This write-up addresses what the metaverse crypto is. It also delves into the advantages, disadvantages, and applications of crypto in this context.
Convergence of Metaverse and Cryptocurrency
As the main form of digital money in the Metaverse, digital currencies can be used to do business and exchange in the digital realm. The term "metaverse" describes a simulation of reality where users can communicate in real time with other users and an environment created by computers. The acquisition and exchange of virtual products, virtual possessions, and electronic creativity within the Metaverse can all be made possible via cryptocurrency.
Many digital currencies are based on blockchain software, which can offer an accessible and safe way to confirm payments and manage digital currencies in the Metaverse. By giving consumers vouchers or other electronic currencies in exchange for their accomplishments or contributions, cryptocurrency might encourage consumer engagement and involvement in the Metaverse.
In the Metaverse, cryptocurrency can also facilitate portable connectivity, enabling users to move commodities and their worth between various virtual settings and platforms.
The idea of fragmentation in the Metaverse, where participants have more ownership and control over their virtual worlds, is consistent with the decentralised characteristics of cryptocurrencies.
Advantages of Metaverse Cryptocurrency
There are countless opportunities for creativity and discovery in the metaverse. Because the blockchain is accessible to everyone, unchangeable, and password-protected, metaverse-centric cryptocurrencies offer greater safety and adaptability than cash. Crypto will be crucial to the evolution of the metaverse as it keeps growing and more individuals show interest in using it. Here are a few of the variables influencing the growth of this new virtual environment.
Safety
Your Bitcoin wallet is intimately linked to your personal information, progress, and metaverse possessions. Additionally, if your digital currency wallet is compromised, especially if your account credentials are weak, public, or connected to your real-world identity, cybercriminals may try to steal your money or personal data.
Adaptability
Digital assets can be accessed and exchanged worldwide due to cryptocurrencies’ ability to transcend national borders. By utilising a local cryptocurrency, many metaverse platforms streamline transactions and eliminate the need for frequent currency conversions between various digital or fiat currencies. Another advantage of using autonomous contract languages is for metaverse cryptos. When consumers make transactions within the network, applications do away with the need for administrative middlemen.
Objectivity
By exposing interactions in a publicly accessible distributed database, the use of blockchain improves accountability. It is more difficult for dishonest people to raise the cost of digital goods and land since Bitcoin transactions are public. Metaverse cryptocurrencies are frequently employed to control project modifications. The outcomes of these legislative elections are made public using digital contracts.
NFT, Virtual worlds, and Digital currencies
Using the NFT is an additional method of using Bitcoin for metaverse transactions. These are distinct electronic documents that have significant potential value.
A creator must convert an electronic work of art into a virtual object or virtual world if they want to display it digitally in the metaverse. Artists produce one-of-a-kind, serialised pieces that are given an NFT that may be acquired through Bitcoin payments.
Applications of Metaverse Cryptography
Fiat money or independent virtual currencies like Robux are used by Web 2 metaverse initiatives to pay for goods, real estate, and services. Fiat lacked the adaptability of cryptocurrencies with automated contract capabilities, even though it may be used to pay for goods and finance the creation of projects. Users can stake these within the network virtual currencies to administer distributed metaverses, and they have all the same functions as fiat currency.
Banking operations
Lending digital cash to purchase metaverse land is possible. Banks that have already made inroads into the metaverse include HSBC and JPMorgan, both of which possess virtual real estate. "We are making our foray into the metaverse, allowing us to create innovative brand experiences for both new and existing customers," said Suresh Balaji, chief marketing officer for HSBC in Asia-Pacific.
Purchasing
An increasingly important aspect of the metaverse is online commerce. Users can interact with real-world brands, tour simulated malls, and try on virtual apparel for their characters. Adidas, for instance, debuted an NFT line in 2021 that included customizable peripherals for the Sandbox. Buyers of NFTs crossed the line separating the virtual universe and the actual world to obtain the tangible goods associated with their NFTs.
Authority
Metaverse initiatives are frequently governed by cryptocurrency. Decentraland, a well-known Ethereum-based metaverse featuring virtual reality components, permits users to submit and vote on suggestions provided they own specific tokens.
Conclusion
The combination of the virtual world and cryptocurrencies creates novel opportunities for trade, innovation, and communication. The benefits of using the blockchain system are increased objectivity, safety, and flexibility. By facilitating exclusive ownership of digital assets, NFTs enhance metaverse immersion even more. In the metaverse, cryptocurrencies are used in banking, shopping, and government, forming a user-driven, autonomous digital world. The combination of cryptocurrencies and the metaverse will revolutionise how we interact with online activities, creating a dynamic environment that presents both opportunities and difficulties.
References
- https://www.telefonica.com/en/communication-room/blog/metaverse-and-cryptocurrencies-what-is-their-relationship/
- https://hedera.com/learning/metaverse/metaverse-crypto
- https://www.linkedin.com/pulse/unleashing-power-connection-between-cryptocurrency-ai-amit-chandra/
Artificial intelligence is revolutionizing industries such as healthcare to finance to influence the decisions that touch the lives of millions daily. However, there is a hidden danger associated with this power: unfair results of AI systems, reinforcement of social inequalities, and distrust of technology. One of the main causes of this issue is training data bias, which appears when the examples on which an AI model is trained are not representative or skewed. To deal with it successfully, this needs a combination of statistical methods, algorithmic design that is mindful of fairness, and robust governance over the AI lifecycle. This article discusses the origin of bias, the ways to reduce it, and the unique position of fairness-conscious algorithms.
Why Bias in Training Data Matters
The bias in AI occurs when the models mirror and reproduce the trends of inequality in the training data. When a dataset has a biased representation of a demographic group or includes historical biases, the model will be trained to make decisions in ways that will harm the group. This is a fact that has a practical implication: prejudiced AI may cause discrimination during the recruitment of employees, lending, and evaluation of criminal risks, as well as various other spheres of social life, thus compromising justice and equity. These problems are not only technical in nature but also require moral principles and a system of governance (E&ICTA).
Bias is not uniform. It may be based on the data itself, the algorithm design, or even the lack of diversity among developers. The bias in data occurs when data does not represent the real world. Algorithm bias may arise when design decisions inadvertently put one group at an unfair advantage over another. Both the interpretation of the model and data collection may be affected by human bias. (MDPI)
Statistical Principles for Reducing Training Data Bias
Statistical principles are at the core of bias mitigation and they redefine the data-model interaction. These approaches are focused on data preparation, training process adjustment, and model output corrections in such a way that the notion of fairness becomes a quantifiable goal.
Balancing Data Through Re-Sampling and Re-Weighting
Among the aforementioned methods, a fair representation of all the relevant groups in the dataset is one way. This can be achieved by oversampling underrepresented groups and undersampling overrepresented groups. Oversampling gives greater weight to minority examples, whereas re-weighting gives greater weight to under-represented data points in training. The methods minimize the tendency of models to fit to salient patterns and improve coverage among vulnerable groups. (GeeksforGeeks)
Feature Engineering and Data Transformation
The other statistical technique is to convert data characteristics in such a way that sensitive characteristics have a lesser impact on the results. In one example, fair representation learning adjusts the data representation to discourage bias during the untraining of the model. The disparate impact remover adjust technique performs the adjustment of features of the model in such a way that the impact of sensitive features is reduced during learning. (GeeksforGeeks)
Measuring Fairness With Metrics
Statistical fairness measures are used to measure the effectiveness of a model in groups.
Fairness-Aware Algorithms Explained
Fair algorithms do not simply detect bias. They incorporate fairness goals in model construction and run in three phases including pre-processing, in-processing, and post-processing.
Pre-Processing Techniques
Fairness-aware pre-processing deals with bias prior to the model consuming the information. This involves the following ways:
- Rebalancing training data through sampling and re-weighting training data to address sample imbalances.
- Data augmentation to generate examples of underrepresented groups.
- Feature transformation removes or downplays the impact of sensitive attributes prior to the commencement of training. (IJMRSET)
These methods can be used to guarantee that the model is trained on more balanced data and to reduce the chances of bias transfer between historical data.
In-Processing Techniques
The in-processing techniques alter the learning algorithm. These include:
- Fairness constraints that penalize the model for making biased predictions during training.
- Adversarial debiasing, where a second model is used to ensure that sensitive attributes are not predicted by the learned representations.
- Fair representation learning that modifies internal model representations in favor of
Post-Processing Techniques
Fairness may be enhanced after training by changing the model outputs. These strategies comprise:
- Threshold adjustments to various groups to meet conditions of fairness, like equalized odds.
- Calibration techniques such that the estimated probabilities are fair indicators of the actual probabilities in groups. (GeeksforGeeks)
Challenges
Mitigating bias is complex. The statistical bias minimization may at times come at the cost of the model accuracy, and there is a conflict between predictive performance and fairness. The definition of fairness itself is potentially a difficult task because various applications of fairness require various criteria, and various criteria can be conflicting. (MDPI)
Gaining varied and representative data is also a challenge that is experienced because of privacy issues, incomplete records, and a lack of resources. The auditing and reporting done on a continuous basis are needed so that mitigation processes are up to date, as models are continually updated. (E&ICTA)
Why Fairness-Aware Development Matters
The outcomes of the unfair treatment of some groups by AI systems are far-reaching. Discriminatory software in recruitment may support inequality in the workplace. Subjective credit rating may deprive deserving people of opportunities. Unbiased medical forecasts might result in the flawed allocation of medical resources. In both cases, prejudice contravenes the credibility and clouds the greater prospect of AI. (E&ICTA)
Algorithms that are fair and statistical mitigation plans provide a way to create not only powerful AI but also fair and trustworthy AI. They admit that the results of AI systems are social tools whose effects extend across society. Responsible development will necessitate sustained fairness quantification, model adjustment, and upholding human control.
Conclusion
AI bias is not a technical malfunction. It is a mirror of real-world disparities in data and exaggerated by models. Statistical rigor, wise algorithm design, and readiness to address the trade-offs between fairness and performance are required to reduce training data bias. Fairness-conscious algorithms (which can be implemented in pre-processing, in-processing, or post-processing) are useful in delivering more fair results. As AI is taking part in the most crucial decisions, it is necessary to consider fairness at the beginning to have a system that serves the population in a responsible and fair manner.
References
- Understanding Bias in Artificial Intelligence: Challenges, Impacts, and Mitigation Strategies: E&ICTA, IITK
- Bias and Fairness in Artificial Intelligence: Methods and Mitigation Strategies: JRPS Shodh Sagar
- Fairness and Bias in Artificial Intelligence: A Brief Survey of Sources, Impacts, and Mitigation Strategies: MDPI
- Ensuring Fairness in Machine Learning Algorithms: GeeksforGeeks
Bias and Fairness in Machine Learning Models: A Critical Examination of Ethical Implications: IJMRSET - Bias in AI Models: Origins, Impact, and Mitigation Strategies: Preprints
- Bias in Artificial Intelligence and Mitigation Strategies: TCS
- Survey on Machine Learning Biases and Mitigation Techniques: MDPI


