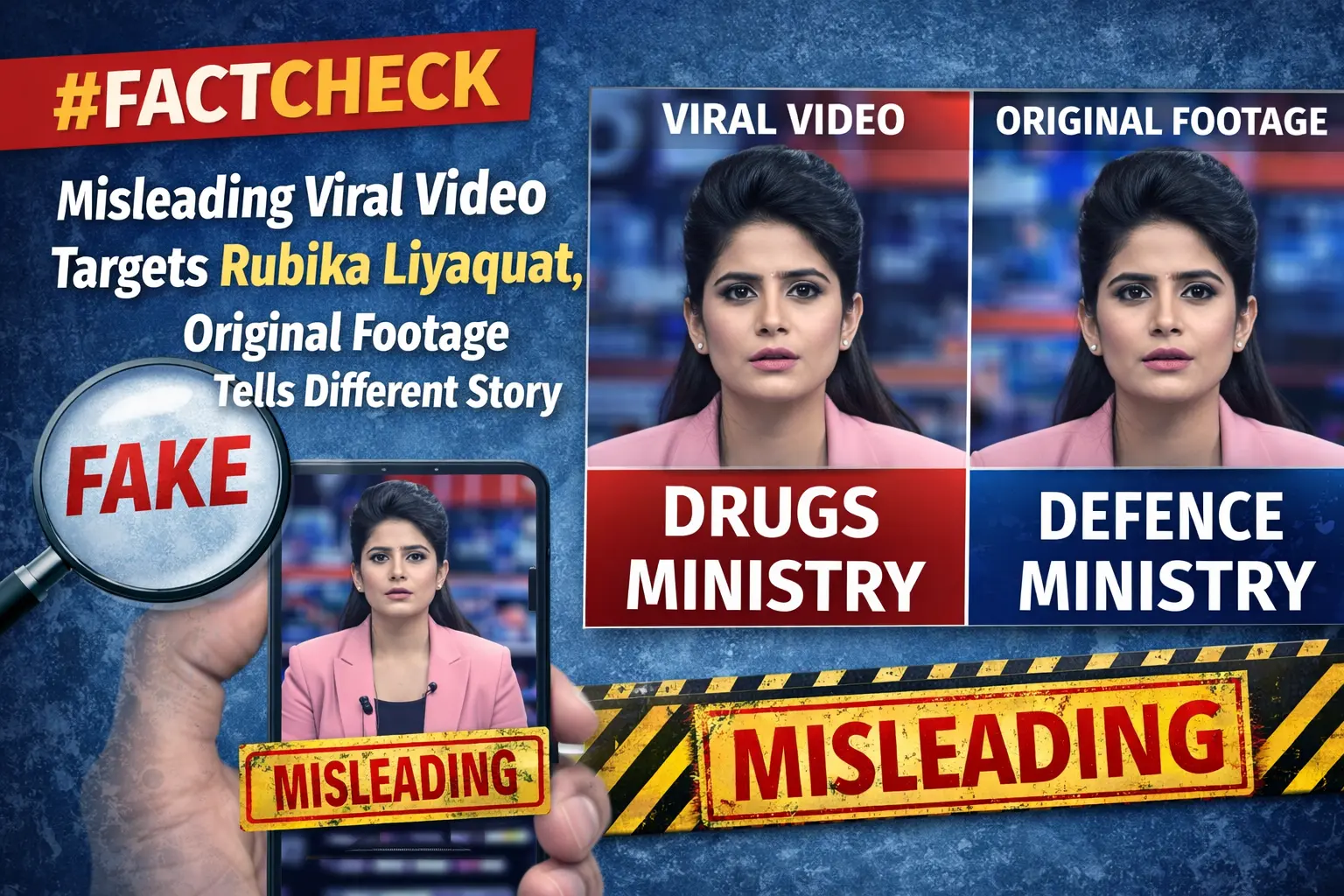
Unseen Shadows: The Silent War of Malware on Mac
Introduction
In the intricate maze of our interconnected world, an unseen adversary conducts its operations with a stealth almost poetic in its sinister intent. This adversary — malware — has extended its tendrils into the digital sanctuaries of Mac users, long perceived as immune to such invasive threats. Our narrative today does not deal with the physical and tangible frontlines we are accustomed to; this is a modern tale of espionage, nestled in the zeros and ones of cyberspace.
The Mac platform, cradled within the fortifications of Apple's walled garden ecosystem, has stood as a beacon of resilience amidst the relentless onslaught of cyber threats. However, this sense of imperviousness has been shaken at its core, heralding a paradigm shift. A new threat lies in wait, bridging the gap between perceived security and uncomfortable vulnerability.
The seemingly invincible Mac OS X, long heralded for its robust security features and impervious resilience to virus attacks, faces an undercurrent of siege tactics from hackers driven by a relentless pursuit for control. This narrative is not about the front-and-centre warfare we see so often reported in media headlines. Instead, it veils itself within the actions of users as benign as the download of pirated software from the murky depths of warez websites.
The Incident
The casual act, born out of innocence or economic necessity, to sidestep the financial requisites of licensed software, has become the unwitting point of compromised security. Users find themselves on the battlefield, one that overshadows the significance of its physical counterpart with its capacity for surreptitious harm. The Mac's seeming invulnerability is its Achilles' heel, as the wariness against potential threats has been eroded by the myth of its impregnability.
The architecture of this silent assault is not one of brute force but of guile. Cyber marauders finesse their way through the defenses with a diversified arsenal; pirated content is but a smokescreen behind which trojans lie in ambush. The very appeal of free access to premium applications is turned against the user, opening a rift that permits these malevolent forces to ingress.
The trojans that permeate the defenses of the Mac ecosystem are architects of chaos. They surreptitiously enrol devices into armies of sorts – botnets which, unbeknownst to their hosts, become conduits for wider assaults on privacy and security. These machines, now soldiers in an unconsented war, are puppeteered to distribute further malware, carry out phishing tactics, and breach the sanctity of secure data.
The Trojan of Mac
A recent exposé by the renowned cybersecurity firm Kaspersky has shone a spotlight on this burgeoning threat. The meticulous investigation conducted in April of this year unveiled a nefarious campaign, engineered to exploit the complacency among Mac users. This operation facilitates the sale of proxy access, linking previously unassailable devices to the infrastructure of cybercriminal networks.
This revelation cannot be overstated in its importance. It illustrates with disturbing clarity the evolution and sophistication of modern malware campaigns. The threat landscape is not stagnant but ever-shifting, adapting with both cunning and opportunity.
Kaspersky's diligence in dissecting this threat detected nearly three dozen popular applications, and tools relied upon by individuals and businesses alike for a multitude of tasks. These apps, now weaponised, span a gamut of functionalities - image editing and enhancement, video compression, data recovery, and network scanning among them. Each one, once a benign asset to productivity, is twisted into a lurking danger, imbued with the power to betray its user.
The duplicity of the trojan is shrouded in mimicry; it disguises its malicious intent under the guise of 'WindowServer,' a legitimate system process intrinsic to the macOS. Its camouflage is reinforced by an innocuously named file, 'GoogleHelperUpdater.plist' — a moniker engineered to evade suspicion and blend seamlessly with benign processes affiliated with familiar applications.
Mode of Operation
Its mode of operation, insidious in its stealth, utilises the Transmission Control Protocol(TCP) and User Datagram Protocol(UDP) networking protocols. This modus operandi allows it to masquerade as a benign proxy. The full scope of its potential commands, however, eludes our grasp, a testament to the shadowy domain from which these threats emerge.
The reach of this trojan does not cease at the periphery of Mac's operating system; it harbours ambitions that transcend platforms. Windows and Android ecosystems, too, find themselves under the scrutiny of this burgeoning threat.
This chapter in the ongoing saga of cybersecurity is more than a cautionary tale; it is a clarion call for vigilance. The war being waged within the circuits and code of our devices underscores an inescapable truth: complacency is the ally of the cybercriminal.
Safety measures and best practices
It is imperative to safeguard the Mac system from harmful intruders, which are constantly evolving. Few measures can play a crucial role in protecting your data in your Mac systems.
- Refrain from Unlicensed Software - Refrain from accessing and downloading pirated software. Plenty of software serves as a decoy for malware which remains dormant till downloaded files are executed.
- Use Trusted Source: Downloading files from legitimate and trusted sources can significantly reduce the threat of any unsolicited files or malware making its way into your Mac system.
- Regular system updates: Regular updates to systems released by the company ensure the latest patches are installed in the system critical to combat and neutralize emerging threats.
- General Awareness: keeping abreast of the latest developments in cyberspace plays a crucial role in avoiding new and emerging threats. It is crucial to keep pace with trends and be well-informed about new threats and ways to combat them.
Conclusion
In conclusion, this silent conflict, though waged in whispers, echoes with repercussions that reverberate through every stratum of digital life. The cyber threats that dance in the shadows cast by our screens are not figments of paranoia, but very real specters hunting for vulnerabilities to exploit. Mac users, once confident in their platforms' defenses, must awaken to the new dawn of cybersecurity awareness.
The battlefield, while devoid of the visceral carnage of physical warfare, is replete with casualties of privacy and breaches of trust. The soldiers in this conflict are disguised as serviceable code, enacting their insidious agendas beneath a façade of normalcy. The victims eschew physical wounds for scars on their digital identities, enduring theft of information, and erosion of security.
As we course through the daunting terrain of digital life, it becomes imperative to heed the lessons of this unseen warfare. Shadows may lie unseen, but it is within their obscurity that the gravest dangers often lurk, a reminder to remain ever vigilant in the face of the invisible adversary.