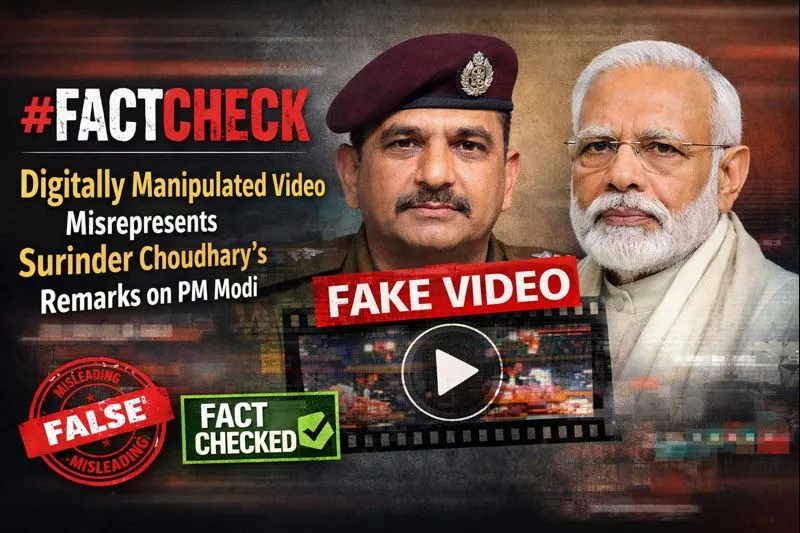
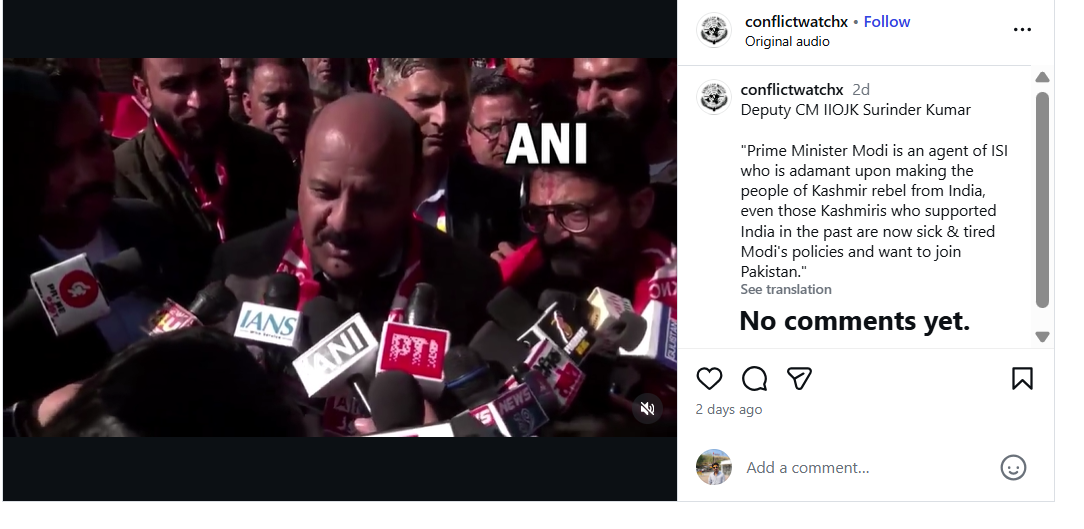
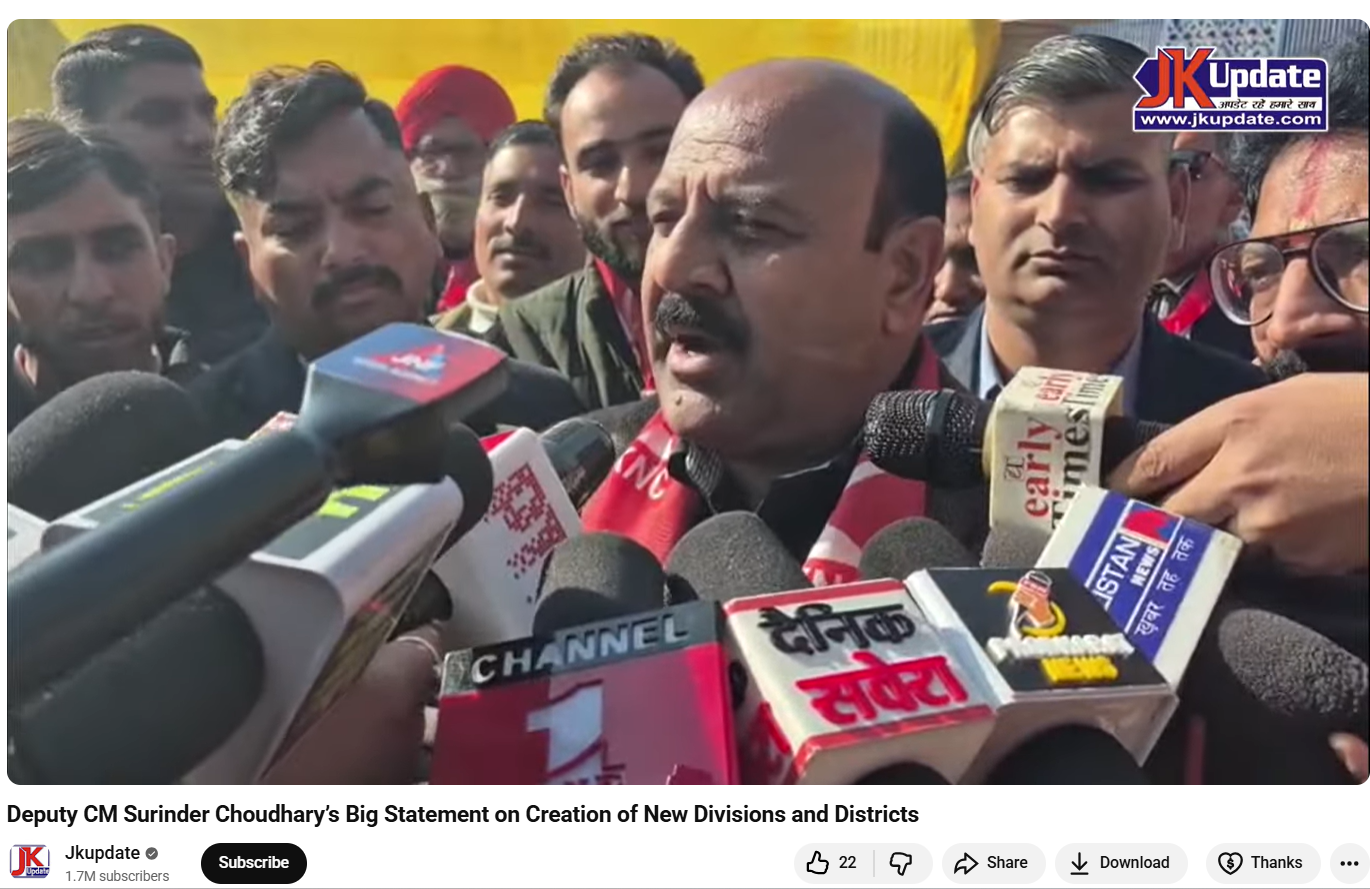
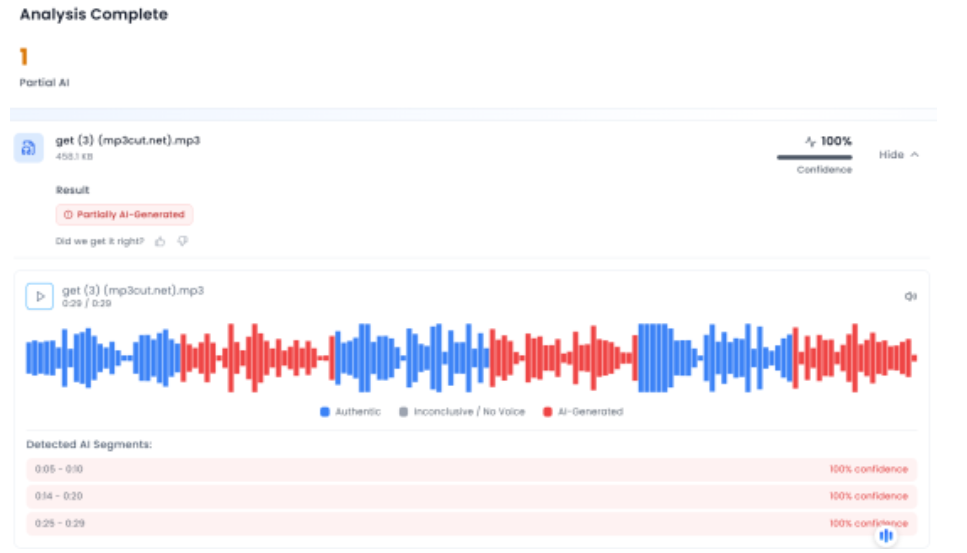
Freedom of Speech and Expression in the Age of Social Media
Introduction
The debate between free speech and social responsibility is one of the oldest, long-running debates in history. Free speech is considered to be at the heart of every democracy. It is considered the “mother” of all other freedoms, enshrined in Article 19(1)(a) of the Indian Constitution under Part III: Fundamental Rights. It takes various shapes and forms according to the sociopolitical context of society. Evelyn Beatrice Hall, a prominent English writer of the 19th century, laid the foundation of every democracy when she wrote in her book, "I disapprove of what you say, but I willdefend to the death your right to say it." The drastic misuse of social media to disseminate propaganda and fakenews makes it a marketplace of half-baked truth, becoming the antithesis ofwhat early philosophers dreamed of for a democratic modern age. Losethe ethics, and there you have it, the modern conceptualisation of freedom ofspeech and expression in the digital age. The right to freedom of speech andexpression is one of the most fundamental rights, but its exercise is notunfettered, and certain limits are placed upon this right under Art. 19 (2).Every right comes with a corresponding duty, and the exercise of such freedomalso puts the citizenry under the responsibility not to violate the rights ofothers and not to use the media to demean any other person.
SocialMedia: The New Public Square or a Weaponised Echo Chamber
InIndia, Art. 19(1)(a) of the constitution guarantees the right to freedom ofspeech and expression, but it is not absolute. Under Art. 19(2), this right issubject to reasonable restrictions in the interest of public order, decency,morality, and national security. This is construed as a freedom for everyindividual to freely express their opinions, but not to incite violence, spreadfalsehoods, or harm others’ dignity. Unfortunately, the boundaries betweenthese are increasingly blurred.
Thedissemination of unfiltered media and the strangulation of innocence by pushingoften vulgar and obscene content down the throats of individuals, withoutverifying the age and gender profile of the social media user, is a big farcein the name of free speech and a conscious attempt by the intermediaries andsocial media platforms such as Facebook, Instagram, Threads, etc., to wriggleout of their responsibility. A prime example is when Meta’s Mark Zuckerberg, on7th January 2025, gave a statement asserting less intervention into what peoplefind on its social media platforms as the new “best practice”. While lessinterference would have worked in a generation that merely operated on thediffering, dissenting, and raw ideas bred by the minds of differentindividuals, it is not the case for this day and age. There has been asignificant rise in cases where social media platforms have been used as abattleground for disputes, spreading communal violence, misinformation, anddisinformation.
Thereis no debate about the fact that social media platforms have fostered a globalexpression, making the world a global village, bringing everyone together. Onthe other hand, the platforms have become the epicentre of computer-basedcrimes, where children and teenagers often become prey to these crimes,cyberbullying, and cyberstalking.
Rising Importance of Platform Accountability
Themost pertinent question that is to be asked with a conscious mind is whether anunregulated media is a reflection of Freedom of Speech, a right given to us byour constitution under Article. 19(1)(a), or whether free speech is just a garbby big stakeholders, and we are all victims of an impending infodemic andvictims of AI algorithms, because, as per the reports that surfaced during theCovid-19 pandemic, India saw a dramatic 214% rise in false information. Anotherreport by the UNESCO-Ipsos survey revealed that 85% of Indian respondentsencounter online hate speech, with around 64% pointing to social media as aprimary source.
While the focus on platform accountability is critical, it is equally important to recognise that the right to free speech is not absolute. Therefore, users also bear a constitutional responsibility while exercising this right. Free expression in a democratic society must be accompanied by civic digital behaviour, which includes refraining from spreading hate speech, misinformation, or engaging in harmful conduct online. The most recent example of this is the case of Ranveer Gautam Allahabadia vs. UOI (popularly known as “Latent Case”); the court came down heavily on the hosts and makers of the show and made its position crystal clear by stating, “there is nothinglike a fundamental right on platter...the fundamental rights are all followedby a duty...unless those people understand duty, there is no [...] deal withthat kind of elements...if somebody wants to enjoy fundamental rights, thiscountry gives a guarantee to enjoy, but guarantee is with a duty so thatguarantee will involve performing that duty also” .
The Way Forward: CyberPeace Suggests
In order to realise the benefits and derive the true benefits from the rights we are provided, especially the one in discussion, i.e., Freedom of Speech and Expression, the government and the designated intermediaries and regulators have to prepare both roadmaps, one for “Platform Accountability” and one for "User Accountability”, wherein the regulators with a reasonable foresight should conduct Algorithm Risk Audits which is a technique to make algorithms and there effects on content feeds visible. It can be an effective tool and an objective manner to compare how algorithms are automatically pushing different content to different users in an unfair or unbalanced way. As for user accountability, “Digital Literacy” is the way forward, ensuring that social media remains a marketplace of ideas and does not become a minefield of misfires.